Key Highlights
- Ransomware on the rise: Global ransomware attacks surged by 67% in 2023, with businesses losing a median of $11,150 per incident and up to $1.2 million in severe cases.
- Traditional defenses aren’t enough: Antivirus and firewalls miss sophisticated attacks that hide in network traffic or exploit unknown vulnerabilities.
- End-to-end visibility: By monitoring east-west and north-south traffic, NDR detects hidden threats that bypass endpoint tools.
- NetWitness advantage: NetWitness enhances NDR with total network visibility, threat intelligence integration, automated response, and forensic investigation for faster containment.
Ransomware is like a thief sneaking into your house, quietly testing locks before stealing everything you own. In 2023, these digital break-ins spiked by 67% globally, with businesses losing a median of $11,150 per attack and up to $1.2 million in the worst cases. Old-school defenses like antivirus software are like rusty padlocks, easily picked by today’s crafty cybercriminals. That’s where Network Detection and Response (NDR) comes in, offering a proactive approach to identifying ransomware before it can encrypt critical data or disrupt operations. So, what is NDR in cybersecurity, and how does it stop ransomware dead in its tracks?
In this article, we explore how network threat detection leverages advanced analytics to detect ransomware, real-world corporate use cases, how NetWitness enhances this capability, and answers common questions about NDR.
Why Early Ransomware Detection Starts with the Network
Ransomware doesn’t strike suddenly — it moves quietly through a network long before encryption begins. Attackers probe weak points, establish persistence, and communicate with external command-and-control servers, often without triggering endpoint alerts. That’s why detecting ransomware on network traffic is one of the most reliable ways to catch threats before they explode.
Modern ransomware threat detection depends on understanding how data moves across your environment. Network-level visibility reveals behaviors that traditional tools miss — like lateral movement, data staging, or suspicious outbound traffic. This makes Network Detection and Response (NDR) not just a tool, but a strategic defense layer.
Unlike reactive antivirus or EDR solutions, NDR focuses on what’s happening between systems. It watches every packet, flow, and connection — identifying subtle patterns that indicate a NDR attack in progress. The best NDR vendors pair this visibility with AI and machine learning to flag anomalies, prioritize threats, and automate responses, cutting detection and response time dramatically.
In short, the earlier your team can see ransomware behavior on the network, the faster you can stop it — before encryption, data loss, or downtime begin.
How Network Detection Response Stops Ransomware
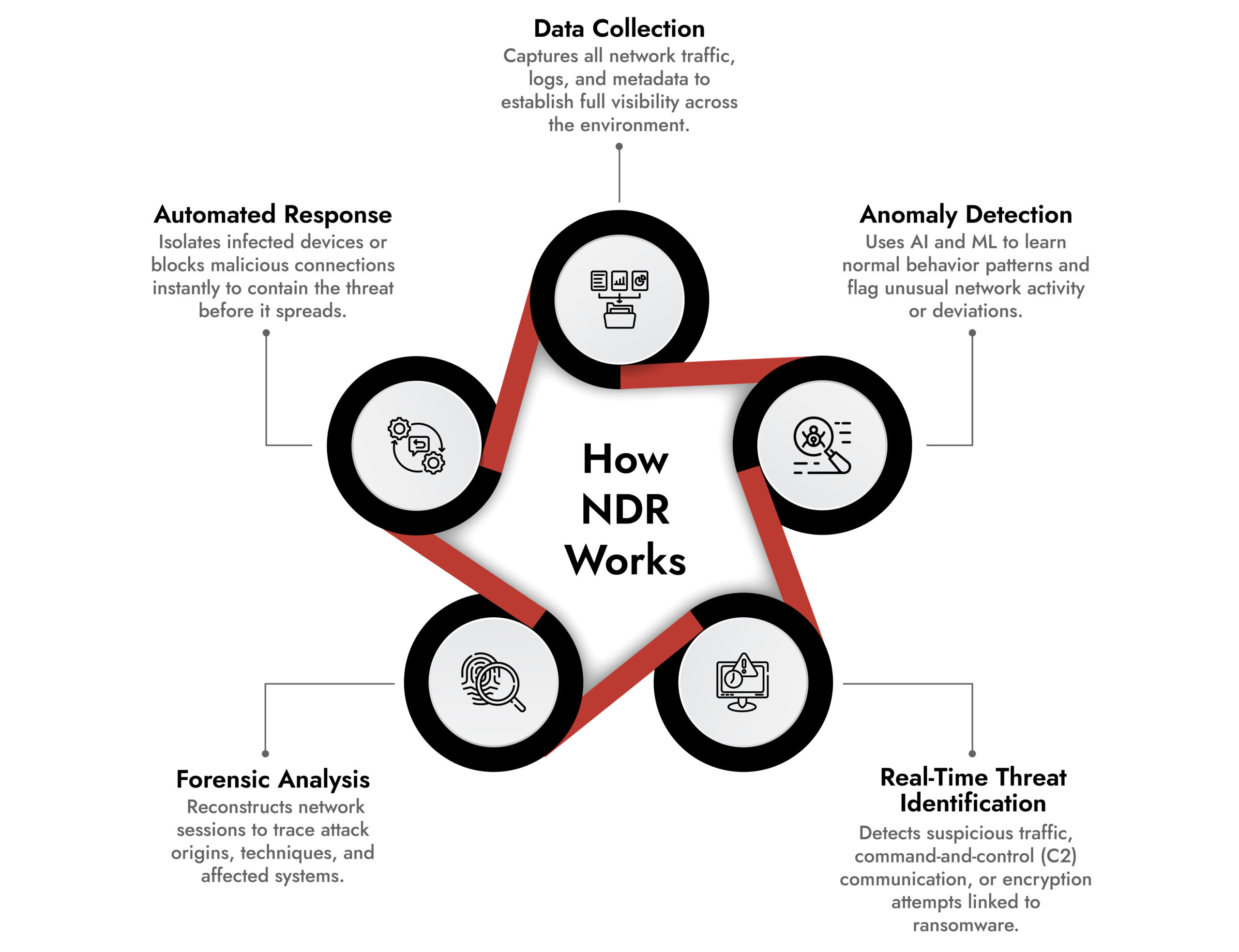
Ransomware often enters networks through phishing emails, compromised credentials, or exploited vulnerabilities, lying dormant before encrypting files or exfiltrating data. NDR detects these threats early by monitoring network traffic for signs of malicious activity across the ransomware kill chain. Here’s how it works:
- Anomaly Detection: NDR uses AI and ML to establish a baseline for normal network behavior. It flags deviations, such as unusual data transfers or connections to command-and-control (C2) servers, which are common in ransomware attacks. For example, an NDR solution identified a Dharma ransomware attack by detecting anomalous RDP connections from rare IP addresses, stopping it before encryption began.
- Real-Time Threat Identification: NDR analyzes network packets to detect early indicators of ransomware activity, such as unusual encryption behavior, communication with known malicious domains, or the delivery of ransom notes over the network. Unlike endpoint-only solutions like RansomWall, which reported 98.25% accuracy in detecting crypto ransomware by monitoring file systems and host-level activity, NDR provides broader, real-time visibility across the network. This allows it to identify and flag ransomware behaviors even before they reach endpoints, reducing dwell time and preventing encryption at scale.
- Forensic Analysis: Post-detection, NDR provides detailed logs, and packet captures for network forensic threat detection, enabling security teams to trace the attack’s origin, scope, and tactics. This helps prevent future incidents and supports compliance with frameworks like NIST and ISO.
- Automated Response: Advanced NDR platforms can isolate infected devices or block malicious connections autonomously, minimizing damage. Organizations with NDR solutions have reported containing threats before they reach the encryption stage, avoiding costly disruptions averaging 24 days per ransomware incident.
Use Cases: NDR in Action
NDR’s ability to detect ransomware early makes it invaluable across industries. Below are three corporate use cases illustrating how network detection response protects organizations:
Healthcare: Protecting Patient Data
A major hospital network faced a ransomware attack targeting its electronic health record (EHR) system. The attacker used a phishing email to gain access, attempting to move laterally to encrypt critical servers. An NDR solution detected unusual network traffic patterns, including connections to a C2 server, and isolated the compromised device within minutes. This prevented data encryption and ensured patient care continuity. With healthcare attacks rising – hospitals were the fifth most targeted industry in 2023 – this use case underscores NDR’s role in safeguarding sensitive data.
Manufacturing: Securing Operational Technology
A manufacturing firm with legacy systems vulnerable to ransomware deployed an NDR platform to monitor its operational technology (OT) network. When a Medusa ransomware variant attempted to exfiltrate data via an FTP server, the NDR system flagged anomalous outbound traffic and blocked the transfer. This saved the company from potential production downtime, which can cost manufacturers millions, as the industry topped the list of ransomware targets in 2023.
Financial Services: Preventing Financial Loss
A financial institution experienced a ransomware attempt via a compromised RDP credential. The NDR solution identified unusual login attempts and blocked connections to a malicious domain, stopping the attack before encryption. With ransomware-related losses reaching $449.1 million in crypto payments in the first half of 2023, NDR’s proactive detection protected the firm from significant financial and reputational damage.
How NetWitness Enhances NDR for Ransomware Defense
As a leading NDR vendor ,NetWitness takes NDR cybersecurity to the next level with its comprehensive, real-time visibility and advanced analytics, specifically designed to combat ransomware and other sophisticated threats. Here’s how NetWitness stands out:
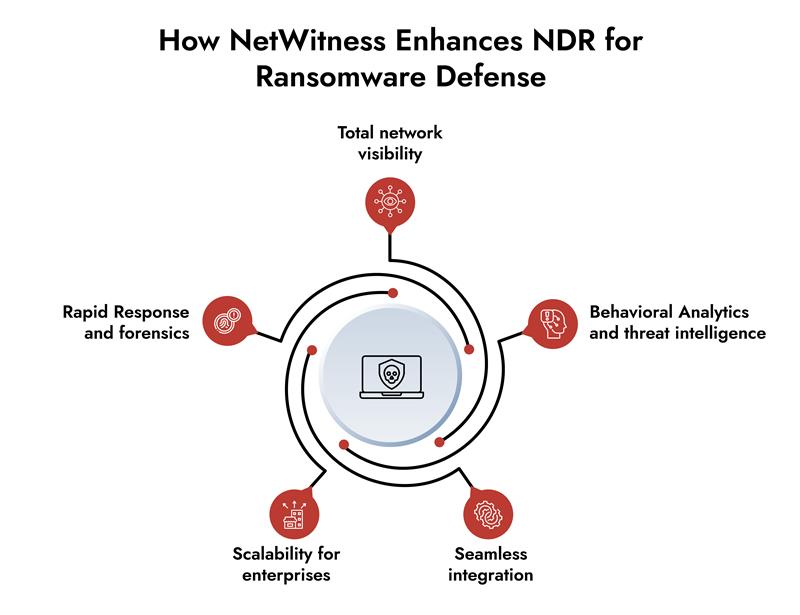
- Total Network Visibility: NetWitness captures all network traffic – on-premises, in the cloud, and across virtual environments – using deep data capture, metadata, and NetFlow. This ensures no ransomware activity goes unnoticed, providing pervasive visibility across hybrid IT infrastructures.
- Behavioral Analytics and Threat Intelligence: By combining behavioral analytics, data science, and threat intelligence, NetWitness detects both known and unknown ransomware threats, such as zero-day attacks, with high accuracy. It enriches log data with contextual information to prioritize high-risk threats and reduce false positives, enabling faster investigations.
- Rapid Response and Forensics:NetWitness integrates with SIEM, SOAR, and EDR solutions, creating a unified defense ecosystem. This interoperability ensures coordinated responses, making it ideal for complex enterprises. For example, NetWitness’s API enables seamless third-party integrations, enhancing SOC workflows.
- Seamless Integration: NetWitness integrates with SIEM, SOAR, and EDR solutions, creating a unified defense ecosystem. This interoperability ensures coordinated responses, making it ideal for complex enterprises. For example, NetWitness’s API enables seamless third-party integrations, enhancing SOC workflows.
- Scalability for Enterprises: Designed for large organizations, NetWitness supports scalable deployments across distributed networks, with large enterprises praising its flexibility and analytics capabilities.
With capabilities built for scale, precision, and speed, NetWitness’s approach has proven effective in real-world scenarios.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.

Why NDR Solution is Essential for Network Security
Ransomware tactics are evolving fast, bypassing traditional defenses like firewalls and antivirus. In fact, ransomware incidents surged more than 90% in 2023, with events like the Conti gang’s $20 million ransom demand on Costa Rica’s government highlighting the high stakes. Here’s how NDR helps modernize your ransomware defense:
- Detecting Unknown Threats – Advanced AI enables NDR to recognize and block even brand-new ransomware variants, achieving a 99.3% detection rate in recent evaluations.
- Accelerating Response – Real-time alerts and contextual analysis help reduce response times by up to 70%.
- Comprehensive Coverage – With full visibility across your network, NDR is critical for 87% of cybersecurity professionals that rely on traffic analysis for threat detection.
- Compliance-Friendly – Detailed logging and forensic capabilities support alignment with frameworks like NIST, making audits and regulatory reporting easier.
Ransomware remains a top cybersecurity threat, but NDR cybersecurity offers a powerful solution to detect and stop attacks before they strike your network. By leveraging network threat detection software and forensic threat detection, NDR software empowers organizations to stay ahead of evolving threats.
Frequently Asked Question
1. What is Network Detection and Response (NDR)?
NDR is a cybersecurity solution that monitors network traffic in real time to detect and respond to threats like ransomware. It uses AI, ML, and behavioral analytics to identify anomalies and provide forensic threat detection for investigations. Learn more in our guide on Understanding NDR: The Foundation of Modern Cybersecurity.
2. How does NDR differ from EDR?
While Endpoint Detection and Response (EDR) focuses on device-level threats, NDR monitors network traffic for both internal (east-west) and external (north-south) activities. NDR complements EDR by catching threats that evade endpoint solutions, such as agentless attacks on IoT devices.
3. Can NDR prevent ransomware attacks?
NDR focuses on early detection and response rather than prevention. By identifying ransomware indicators like anomalous traffic or C2 communications, NDR stops attacks before they cause significant damage. Solutions like NetWitness enhance this with automated responses.
4. Why choose NetWitness for NDR?
NetWitness offers full-packet capture, advanced behavioral analytics, and seamless integration with SIEM and SOAR systems, making it ideal for enterprises. Its scalability and high detection rates make it a trusted choice in the NDR category. Explore NetWitness NDR solutions for details.
5. How does NDR support compliance?
NDR provides detailed logs and forensic data to meet regulatory requirements like NIST and ISO. NetWitness, for example, supports compliance by offering comprehensive visibility and audit-ready reports.




