Cyber threats don’t operate in isolation, so why should your defenses? Let’s be honest, most organizations already have Endpoint Detection and Response (EDR) in place. It has become a foundational part of any security program. But as attackers get smarter, EDR alone isn’t enough. What many security teams are still missing is Network Detection and Response (NDR). And without it, you are flying blind across large parts of your network.
So, the question isn’t really “Which is better – NDR or EDR?”
It’s this: How do you close the visibility and detection gaps that EDR can’t cover?
In this blog, we will compare NDR vs EDR for threat detection, show how they complement each other, and explain why adding NDR completes your defensive picture.
What Is EDR (Endpoint Detection and Response)?
EDR tools detect and respond to threats at the endpoint level – your laptops, desktops, mobile devices, and servers. They monitor behavior, flag suspicious activity, and help contain attacks quickly.
Key Functions of EDR:
- Monitors endpoint activities such as file execution, registry changes, and user behavior
- Detects malware, ransomware, and exploits targeting endpoints
- Supports threat hunting through historical endpoint data
- Allows for remote remediation of compromised devices
EDR is essential for endpoint visibility.
But here’s the catch: attackers don’t just hit endpoints. Once inside, they often move laterally – across networks, through unmanaged devices, or via encrypted traffic. That’s where EDR loses sight.
What Is NDR (Network Detection and Response)?
While EDR watches what’s happening on the device, NDR watches everything between devices. It continuously analyzes network traffic- on-prem, cloud, and hybrid- to detect threats that other tools miss.
Think of it as security camera footage for your entire digital environment, not just motion sensors at the door.
NetWitness Network Detection and Response (NDR) excels in this space. It captures full packets, analyzes metadata, and correlates behaviors with threat intelligence to identify known and unknown threats.
Key Features of NetWitness NDR:
- Full Packet Capture: Deep analysis of raw traffic data
- Threat Detection: Behavioral analytics and AI-powered insights
- Forensic Investigation: Reconstruct full network sessions
- Encrypted Traffic Analysis: Flags suspicious encrypted traffic without decryption
- SIEM & EDR Integration: Works with other tools for faster, coordinated response
NDR vs EDR: A Side-by-Side Comparison
| Feature | EDR | NDR |
| Focus Area | Endpoints (devices) | Network traffic |
| Visibility | Device-level events | Lateral movement, unknown devices |
| Threat Detection | Malware, ransomware | Encrypted attacks, lateral movement |
| Forensic Investigation | Endpoint logs | Full network session reconstruction |
| Alert Fatigue Management | Endpoint-centric triage | Contextual alerts across network |
| Use Case Fit | Device-focused orgs | Distributed/hybrid/cloud environments |
Real-World Use Cases: When to Choose Each
Choose EDR if:
- Your infrastructure is endpoint-heavy and centralized
- You require real-time protection from malware or insider threats
- You need endpoint forensics and remote remediation tools
Choose NDR if:
- Your organization has hybrid or multi-cloud environments
- You face visibility gaps due to encrypted or east-west traffic
- You want deeper forensic capabilities beyond the endpoint
- You are struggling with alert fatigue and delayed response
In reality, most organizations need both. One detects what hits the device. The other detects everything around it.
Why EDR Alone Is Not Enough
Here’s the thing: modern attackers don’t care how well you have protected your endpoints because they will just go around them.
They will:
- Use unmanaged devices
- Exploit east-west network paths
- Hide inside encrypted traffic
- Live off the land using native tools
These tactics are invisible to most EDR tools. That’s where NDR solution steps in.
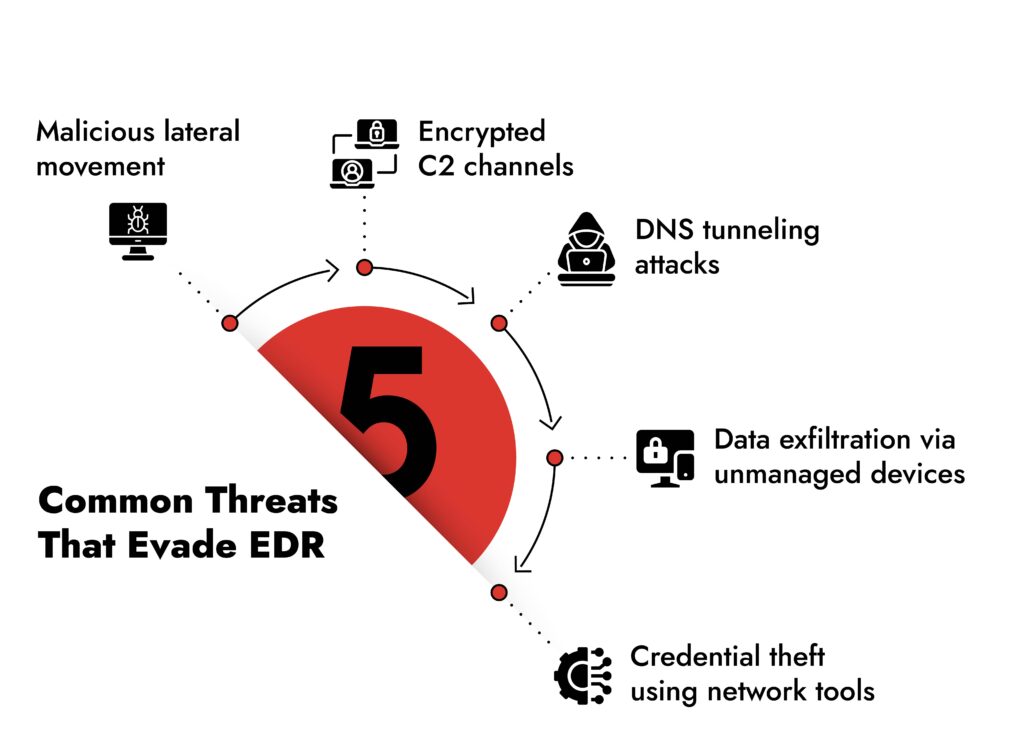
Threats That Only NDR Can Catch
Studies show traditional endpoint tools miss threats like:
- Malicious lateral movement
- Encrypted command-and-control channels
- DNS tunneling
- Credential theft via network tools
- Data exfiltration from unmanaged devices
NetWitness NDR solution fills those gaps with AI, behavioral analytics, and packet-level visibility.
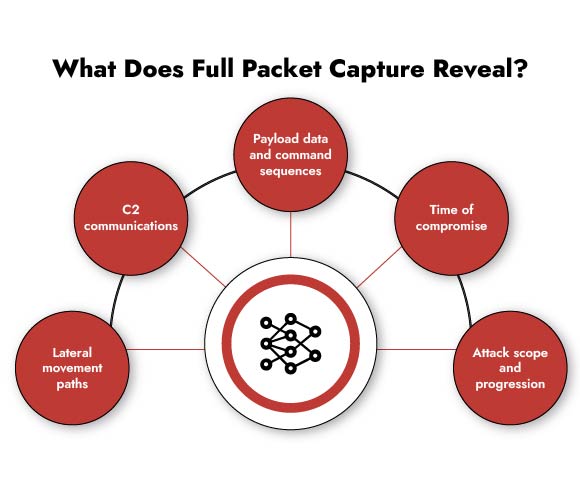
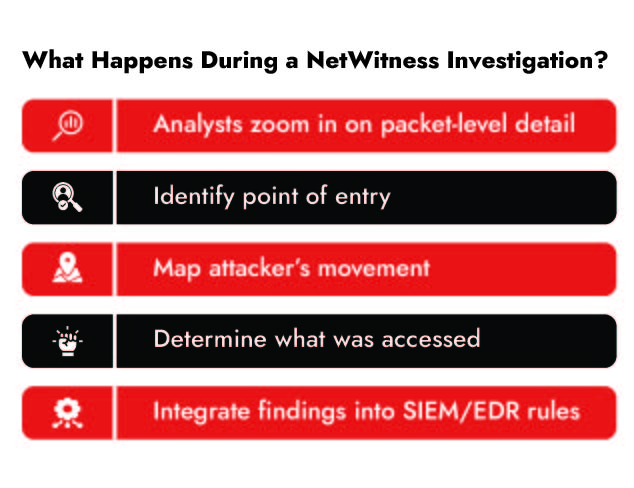
Why Forensics Matter and How NetWitness Excels
Detecting a threat is step one. The next step is understanding what happened, fast.
That’s where NetWitness really shines. With full-packet capture, enriched metadata, and cross-tool correlation, you don’t just spot the threat, you trace its entire path.
What NetWitness NDR solution Enables:
- Reconstruct sessions to see attacker behavior
- Visualize the full timeline of compromise
- Trace lateral movement and pivot points
- Feed findings back into your detection strategy
Still Debating NDR vs EDR? Ask Yourself This:
- Do you have BYOD (bring your own device) or unmanaged devices?
- Are you using multiple clouds or hybrid networks?
- Have you dealt with lateral movement or encrypted threats?
- Do your analysts spend hours chasing false positives?
If your answer is “yes” to two or more, NDR is essential for you.
The Smarter Approach: NDR + EDR Together
This isn’t an either/or decision. NDR and EDR are not competitors; they are complements. For maximum visibility and effective response, organizations should deploy both, ideally integrated into a broader detection and response ecosystem.
Together, they deliver:
- Full-spectrum visibility from device to network
- Faster, smarter response through correlation
- Stronger forensics for post-incident analysis
- Reduced dwell time through early detection
NetWitness supports this unified approach by integrating NDR, EDR, SIEM, and threat intelligence, giving your team one connected view, not siloed snapshots.
Why NetWitness NDR Stands Out
NetWitness is recognized for delivering advanced capabilities that matter most to security teams:
- Deep forensics built on full-packet capture
- Visibility into encrypted and cloud environments
- Seamless integrations with EDR and SIEM
- AI-driven detection of stealthy, lateral threats
- Actionable alerts that cut through the noise
NetWitness helps you see what EDR can’t, and that changes everything.
What sets NetWitness apart is its ability to correlate endpoint and network activity in one unified view, giving analysts the complete story, not disconnected signals.
Final Thoughts: EDR vs NDR Cybersecurity Is Not Either/Or
In the modern threat landscape, relying on endpoint visibility alone leaves your defenses vulnerable. Equally, relying solely on network-level detection might miss device-centric threats.
The smart choice? You need both. And you need them to work together.
Implement a layered detection strategy, EDR plus NDR. That means you:
- Detect threats earlier
- Investigate faster
- Respond smarter
NDR complements EDR by adding deep visibility, advanced forensics, and context-aware threat detection, especially important in today’s complex, encrypted, and hybrid networks.
With NetWitness NDR, your organization gains:
- Unmatched network visibility
- Accelerated detection and response
- Rich forensic analysis to guide post-incident decisions
With NetWitness NDR, you’re not just reacting. You’re understanding. You’re anticipating. And that’s how you stay ahead.
Frequently Asked Questions
1. What is the difference between EDR and NDR?
EDR focuses on endpoints like laptops and servers, monitoring activity and enabling response. NDR monitors network traffic to detect threats moving across devices or using encrypted channels.
2. Which is better: NDR or EDR?
Neither is inherently better. NDR excels at detecting lateral movement and encrypted threats; EDR is strong in direct endpoint protection. The best strategy combines both.
3. How does NetWitness NDR support forensic investigations?
NetWitness provides full packet capture, metadata analysis, and behavioral detection, enabling security teams to reconstruct entire attack chains for detailed investigation.
4. Can NetWitness integrate EDR and NDR?
Yes. NetWitness integrates across EDR, NDR, and SIEM, creating a unified detection and response platform that eliminates blind spots and improves investigation speed.



