NetWitness is happy to be part of the NOC again for another global event by Black Hat in Singapore. The Black Hat Network Operations Center (NOC) delivers a secure, reliable network in one of the most challenging environments in the world. This is done with the support of top-notch solutions providers and experienced security and engineering teams led by Black Hat’s ’ respected NOC Team Leads. The team ensures the security, performance, and visibility of a world-class enterprise network. The NOC Team is always incredible and it’s a privilege to work with them. In the team we are joined by Arista, Cisco, Corelight, MyRepublic and Palo Alto Networks.
The NetWitness Platform
NetWitness upgraded to the latest version that came out in March. The NetWitness version that we use at Black Hat is 12.4. We chose to install the latest version because it has new features that are useful for the tasks during the Black Hat. We can highlight the new Mitre Attack framework mapping, the new quick respond action and last but not least the new OS. Since version 12.4, NetWitness has stopped using CentOS.
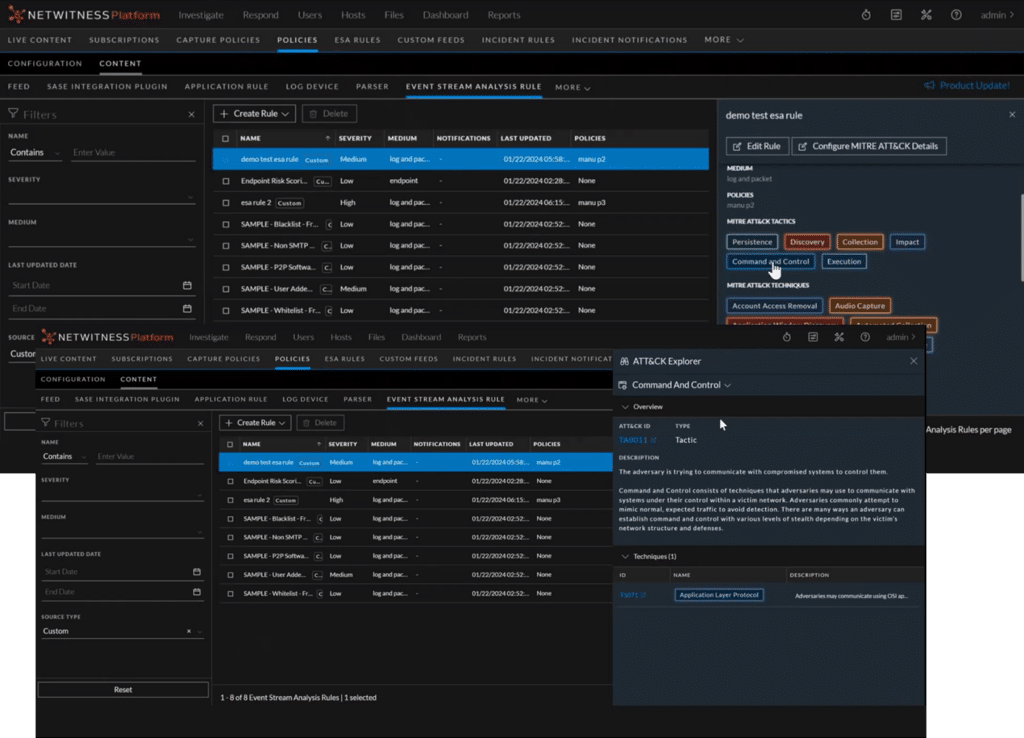
These new features are very important for the NOC’s daily activities to ensure stability, the detection and the response to the event.
The Installed Components
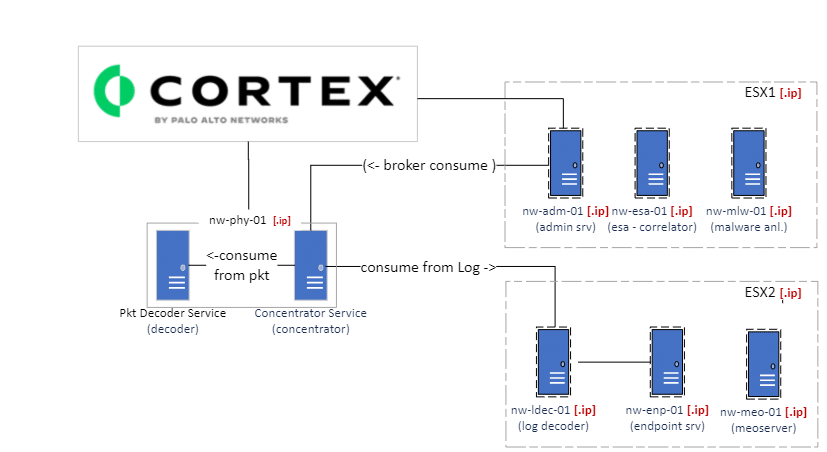
The implemented NetWitness architecture is a straightforward but comprehensive one.
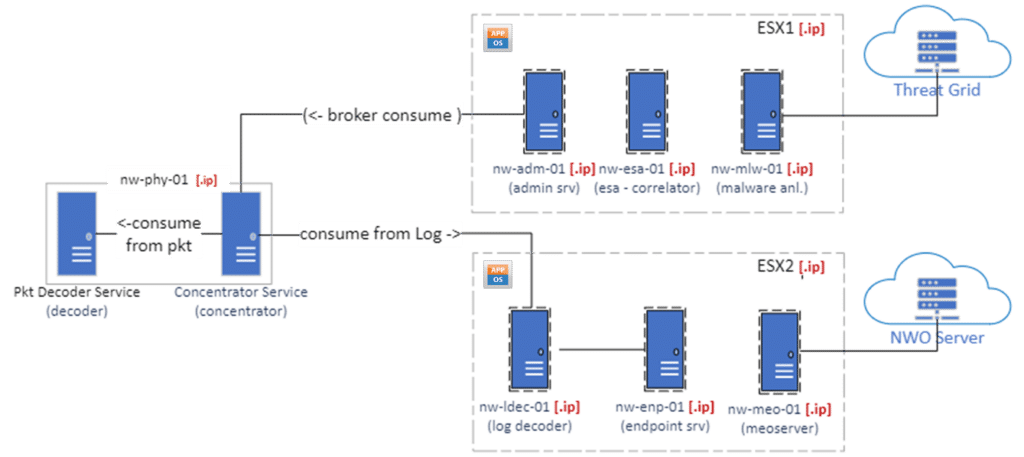
We have a packet decoder, to capture all the traffic from the Black Hat Network. A Log Decoder to collect logs from all the devices and servers on the Black Hat Network and an Endpoint server to monitor the Registration server, a crucial asset of the event.
Analyzing the high level of the architecture we can identify the most important parts.
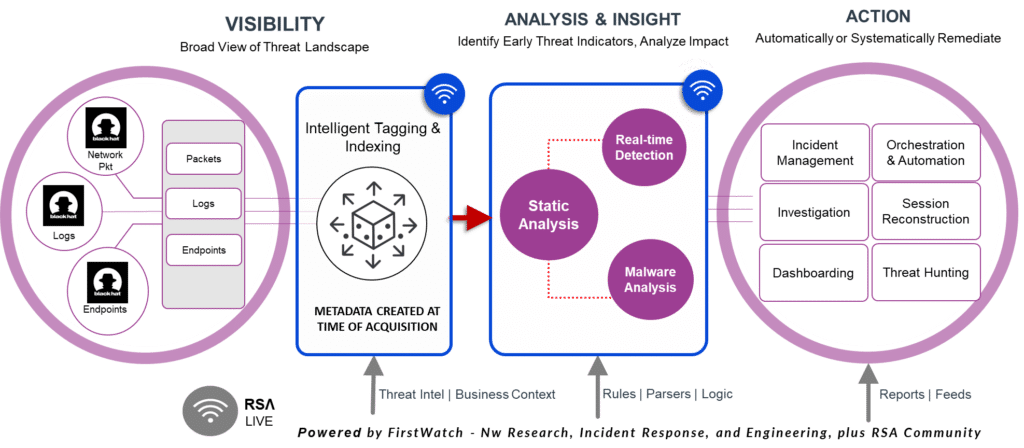
Visibility
The first key factor of the platform and for the Black Hat NOC is visibility. The visibility allows the analyst to see the full range of the events. It doesn’t matter if they are related or not to an anomaly or an incident. All the raw events are gathered as they are. During the Black Hat we have three different sources:
The NetWitness Log Decoder
(with the log collector) is the device that collects and parses log data from various sources on the Black Hat Network, such as firewalls, servers, applications, and endpoints. The Log Decoder normalizes the log data into a common format and enriches it with metadata, such as geo-location, threat intelligence, and user behavior. The Log Decoder enables the NOC team to monitor and investigate the activity and identify any anomalies, threats, or incidents that may occur during the event by checking the system logs. System logs are useful also to detect anomalies and maintain monitored stability.
One of the other relevant log sources is Corelight, they provide additional visibility to network traffic and known security events.
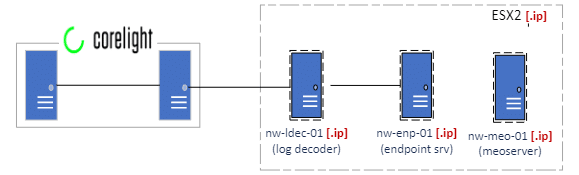
The NetWitness Packet Decoder
is a device that captures and analyzes all the network traffic from the Black Hat Network. The Packet Decoder reconstructs the network sessions and extracts the relevant information, such as protocols, applications, content types, and threat indicators. The Packet Decoder also compresses and stores the raw packet data for full-packet capture and forensics. The Packet Decoder allows the NOC team to have a complete visibility of the network activity and perform deep analysis of any suspicious or malicious events that may occur during the event.
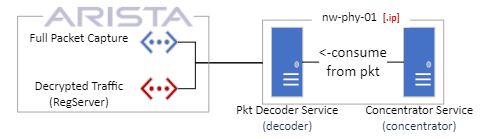
The Network mirroring during the Black Hat is guaranteed from Arista that can provide to the platform both traffic. The complete traffic from the show and the decrypted traffic to and from the Reg Server. This is important to have the full picture and analysis keep the asset monitored.
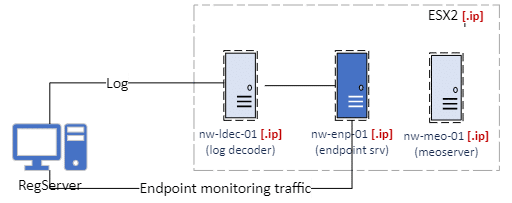
The NetWitness Endpoint server
is a device that collects and analyzes data from the endpoints. The Endpoint server deploys agents on the endpoints to monitor the processes, files, network connections, and user activities. The Endpoint server uses behavioral analytics to detect any anomalies or indicators of compromise on the endpoints, such as malware, ransomware, phishing, or lateral movement. The Endpoint server also provides the NOC team with the ability to continuously monitor the Register Server. The most important Black Hat server responsible for the user registration.
The data collection enrichment process enhances the value of the data collected. It adds more meaning and context to the raw data from different sources on the Black Hat Network. The enrichment helps the NOC team understand the data and the network events better. For example, Enrichment tags all events with the network scope, such as a training room, the show room, the arsenal, etc.
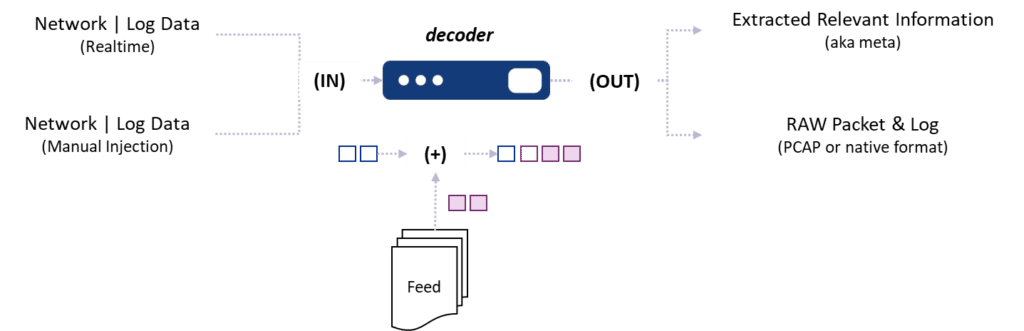
This is very useful for the analyst, because they can focus on real events and ignore legitimate events. The NetWitness Platform also gets enrichment from NetWitness Firstwatch, which is a group of security experts who continuously keep an eye on the threat environment and provide intelligence feeds to the platform. These feeds contain indicators of compromise (IOC), which are bits of information that can help to detect malicious behavior or actors on the network. By adding these IOC to the data, the NetWitness Platform can warn the NOC team of any possible attacks or breaches on the Black Hat Network and assist them to react quickly and effectively.
Analysis and Insight
Analysis & Insight is an important feature of the NetWitness platform leverage during the NOC Analyst activities. The platform can analyze the collected event and data extracted to detect behavior or pattern that are considered bad, uncommon or anyway not compliant to the Black Hat code of conduct.
The Decoder uses its logic to perform static analysis, which can dissect raw events and extract data from them. In this phase, the event processor logic in the decoders can detect relevant patterns or anomalies. Additionally, more static logic is designed and tailored for the NOC Activity.
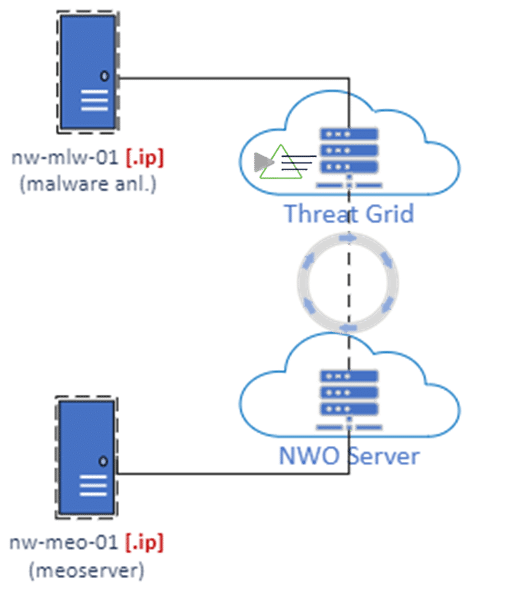
Specific patterns, as a correlation of different event events, are identified from the correlator server. The NetWitness Event Stream Analysis (ESA) server is a device that correlates and analyzes data from multiple sources on the Black Hat Network, such as Log Decoder, Packet Decoder, and Endpoint server. The ESA server uses specific rules and models to detect complex and stealthy threats that may evade traditional detection methods. The ESA server also generates alerts and notifications for the NOC team to prioritize and respond to the most critical incidents.
Specific analysis against the file captured from the network packet decoder is the Malware analysis. The NetWitness Malware Analysis server is a device that performs dynamic and static analysis of suspicious files and objects collected from the Black Hat Network. The Malware Analysis server executes the files in a sandbox environment (for the NOC is the Cisco Threat Grid) and observes their behavior, such as registry changes, network connections, file operations, and system calls.
The Malware Analysis server also extracts the metadata, signatures, and indicators of compromise from the files and compares them with threat intelligence sources. The Malware Analysis server provides the NOC team with detailed reports and risk scores for the files and objects, as well as recommendations for remediation and prevention. An important role with the Malware Analysis is the integration with the Cisco Threat Grid sandbox. All the samples that appear unknown and suspicious to the static malware analysis are sent directly to Cisco TG and submitted for the Dynamic Analysis. This is important for the sandbox. This will reduce drastically the submission optimizing the performance and speed up the malware analysis process.
Action
At the end of our chain there are all the interactions with the NOC Analyst. All the data collected and raised alert are analyzed managed from the automation and orchestration systems and finally from the analyst. On NetWitness side the importance automatically is implemented using the NW Orchestrator.
The NetWitness Orchestrator is a platform that automates and orchestrates the response to security events across the Black Hat Network. It integrates with the NetWitness Malware Analysis and Packet decoder to Cisco Security Malware Analytics, to provide an additional overview and enrichment from the sample collected and analyzed. Moreover, leveraging the new quick response action integration included in 12.4, The NetWitness Orchestrator allows the NOC team to quickly execute playbooks and analyze samples and eventually identify malware.
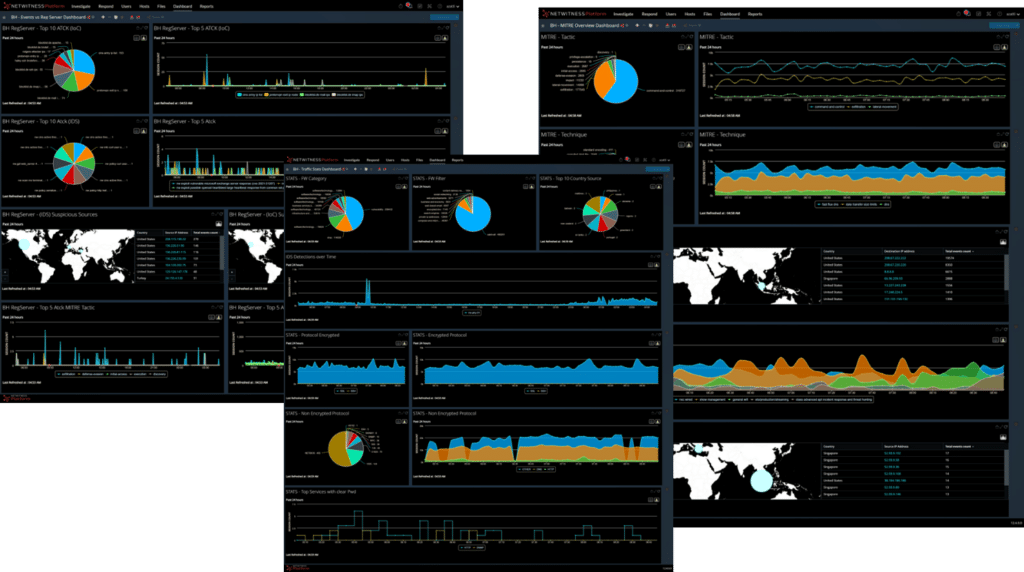
The NOC team can also benefit from the dashboard feature of NetWitness, which provides a comprehensive and customizable view of the network security events. The dashboard can display various widgets that show metrics, charts, tables, maps, and other visualizations of the data collected and analyzed by NetWitness. The dashboard can help the NOC team to monitor the network activity, identify trends and anomalies, prioritize incidents, and track the performance of the security operations. The dashboard can also be customized to meet the specific needs and preferences of each analyst or role. The dashboard is an important tool for the NOC team to gain visibility and insight into the network security posture and to respond effectively to threats.
At the end we must mention the Hunting Activities. Another key feature of NetWitness is the security hunting capability, which enables the NOC team to proactively search for threats and malicious activities in the network. The NetWitness Platform provides a user-friendly interface that allows the analysts execute queries using various filters, operators, and logic expressions. The queries are based on metadata, content, or behavior attributes of the network traffic, such as IP addresses, protocols, ports, domains, files, users, processes, services, and so on. The NetWitness Hunter also supports advanced techniques such as pivot, drill-down, and aggregation, which help the analysts to explore and refine the results of their queries. This NetWitness feature can help the NetWitness NOC team to identify hidden or unknown threats, verify hypotheses, validate alerts, and discover new patterns and indicators of compromise.
The NetWitness hunter team is a specialized group of analysts who use the NetWitness Platform to conduct proactive and reactive threat hunting activities together with the rest of the Black Hat NOC Team. The target is to protect the important assets of Black Hat, this includes the registration servers and Black Hat Network, and collaborate with the NOC Team to guarantee the network and system stability. The NetWitness hunter team for the Black Hat NOC search for signs of compromise, investigate incidents, and uncover new threats in the network and share information, insights, and best practices. The full packet capture and visibility of the NetWitness Platform across all the other tools available in the NOC is important for these activities. Full visibility of the network permits users to better contextualize detected behavior and/or reveal hidden activities not identified from specific alerts.
Finally, the integrations. The platform is fully integrated with the rest of the NOC platform via API’s. This is an important and relevant feature. We have already described the integration with Cisco Security Malware Analytics. Another relevant integration is with Palo Alto xSOAR that permits us to automate different activities behind the NOC tasks and simplify the day-by-day activities.
In this day one article, we have described the main features and benefits of using NetWitness Platform installation in the Black Hat NOC and some details about the architecture. We have highlighted how NetWitness Platform can provide comprehensive visibility, analysis, and detection of network traffic, as well as support security hunting and incident response activities. We have also shown how NetWitness Platform is fully integrated with the rest of the tools in the NOC via API, enabling a seamless and efficient workflow. NetWitness Platform, together with the other vendors that participate in the Black Hat NOC team, represents a powerful and versatile solution that help the Black Hat NOC team protect their assets, identify and respond to threats, and improve security and network stability.



