SIEM, short for Security Information and Event Management, has long been the go-to solution for enterprise threat detection and compliance. It collects log data, monitors activity across the environment, and alerts security teams to suspicious events.
Sounds like a solid foundation, right?
Here’s the thing: while SIEM software plays a vital role in any security strategy, relying on it alone isn’t just outdated, it’s dangerous. Attackers have gotten smarter. The threat surface has exploded. And traditional SIEMs are struggling to keep up.
Let’s break down what SIEM in cybersecurity really is, what it does well, where it falls short, and why modern security demands complete visibility, paired with context, as the foundation for true intelligence.
What Is SIEM in Cyber Security?
At its core, SIEM in cyber security is a centralized system that collects and analyzes security data from across your IT infrastructure. The goal is to detect changes and behaviors that indicate potential threats so you can investigate incidents and support compliance initiatives.
In practice, a SIEM software:
- Aggregates logs from endpoints, servers, network devices, applications, and cloud services
- Normalizes and correlates those logs to identify patterns and anomalies
- Triggers alerts based on predefined rules or detection logic
- Helps security teams investigate incidents and demonstrate regulatory compliance
So when someone asks, What is SIEM in cybersecurity?, think of it as the central repository for logs and security events. In the classic cybersecurity stack, SIEM in cybersecurity serves as the core system for security monitoring, collecting data from across your environment and surfacing anything that looks suspicious. But on its own, it doesn’t make decisions. Just like a CCTV system or a flight recorder, it captures activity. Interpreting that activity, deciding what’s a real threat and what’s noise, still requires human analysts or AI-driven tools layered on top.
Where Traditional SIEM Delivers Value
Let’s not dismiss the value of SIEM. A well-implemented SIEM can:
- Centralize security auditing
- Correlate multi-source events
- Generate compliance reports
- Serve as the investigative source during security incidents
- Offer long-term retention of security data
Security Information and Event Management is a foundational element of any enterprise-grade cybersecurity strategy. Regulatory bodies across the globe increasingly expect organizations to have centralized log management, threat detection, and forensic capabilities in place, all of which SIEM enables. But the effectiveness of a SIEM software still hinges on how well it’s tuned, integrated, and staffed. Without that operational maturity, even the most powerful SIEM can become a source of noise rather than insight.
The Limits of Traditional SIEM テクノロジー
SIEM technology was designed in a different era, when environments were mostly on-premises, cloud services were minimal, and threats were more straightforward. Today’s threat landscape is anything but simple.
Here’s where traditional SIEMs begin to break down:
1. Alert Overload and Fatigue
Most SIEMs flood analysts with alerts, many of which are false positives or noise. A 2023 research study by Devo found that 63% of SOC teams regularly ignore alerts due to volume fatigue, risking true threats slipping through the cracks.
2. Too Much Data, Not Enough Context
SIEM logs collect logs, but logs alone aren’t always enough to tell the full story. Without behavioral context or packet-level data, detecting advanced threats like lateral movement or insider attacks becomes guesswork.
3. Blind Spots in Cloud and Hybrid Environments
Modern IT environments are dynamic, often spanning on-prem infrastructure, public cloud platforms, and containerized or serverless workloads. While traditional SIEM logs struggled to ingest telemetry from these diverse sources, many next-generation solutions have closed that gap, offering integrations via APIs, cloud-native agents, and serverless functions.
Still, challenges persist. Cloud log data alone often lacks the granularity needed to fully reconstruct sophisticated attack paths. And as environments grow more ephemeral and identity-driven, SIEM log management that rely solely on static rules or uncorrelated log data may miss subtle indicators of compromise. Without additional context from network or endpoint sources, even modern SIEMs can leave visibility gaps in critical areas.
4. Heavy Operational Overhead
SIEM tools can be complex and resource intensive. They require ongoing tuning, rule creation, and infrastructure scaling. Without a mature SOC or automation layer, they can become more of a liability than an asset.
5. Lack of Real-Time, Adaptive Detection
Static rules can’t keep pace with fast-evolving attack techniques. Sophisticated threats often bypass detection because SIEM log management has not been updated fast enough or simply can’t adapt in real-time.

Why SIEM Alone No Longer Cuts It
Security decision-makers realize that SIEM is necessary but not sufficient. It’s like using CCTV to guard your house – it shows you something happened, but not always how, why, or what to do about it.
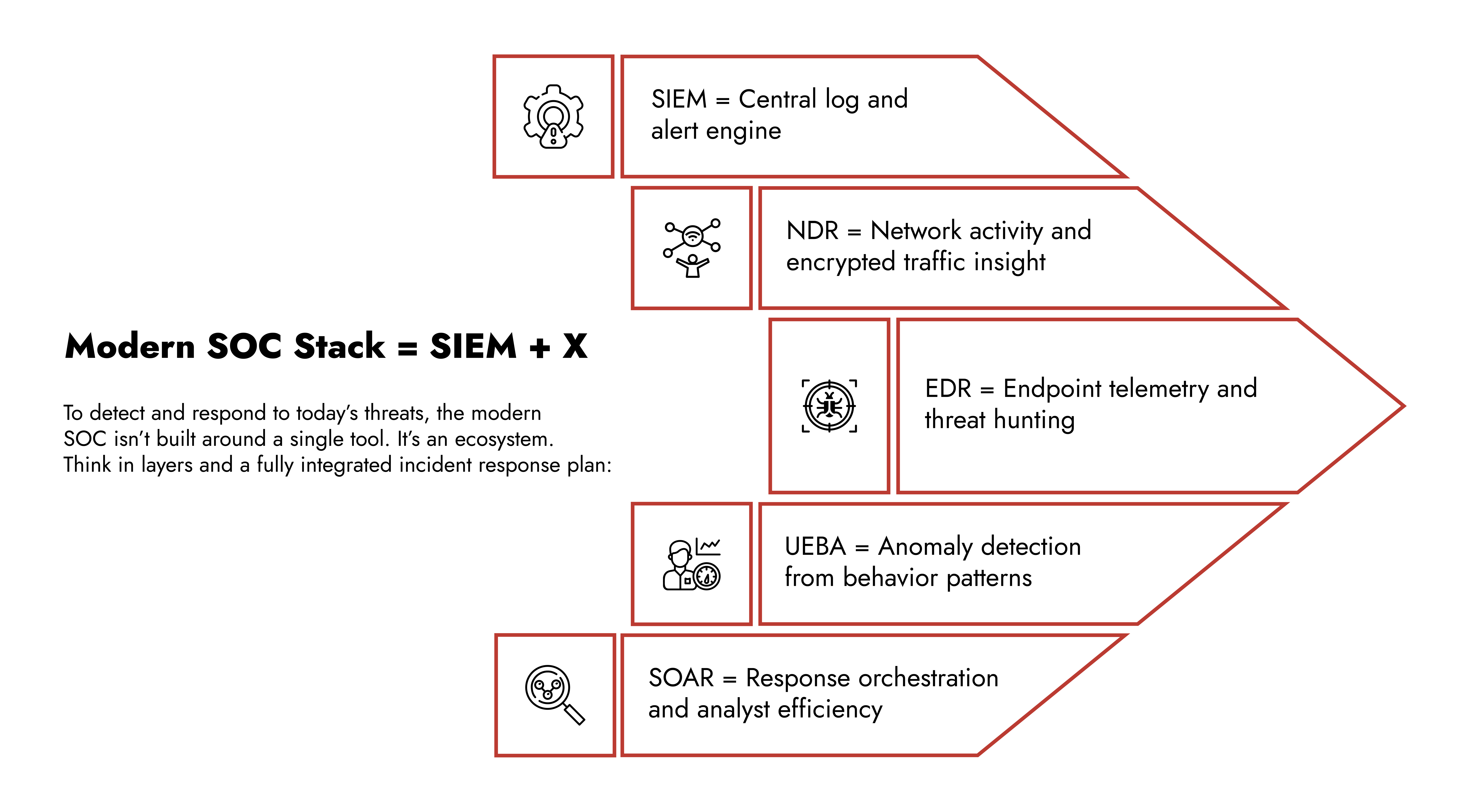
To fill these gaps, organizations are pairing SIEM with:
- Network Detection and Response (NDR): For deep packet inspection and lateral movement visibility
- Endpoint Detection and Response (EDR): For device-level forensics and behavioral threat detection
- ユーザーとエンティティの行動分析(UEBA): For detecting insider threats and account compromise
- SOAR platforms: To automate repetitive tasks and streamline incident response workflows
These technologies provide the context and correlation that SIEM often lacks.
Enter NetWitness SIEM: A Smarter, Context-Aware Approach
NetWitness takes a different approach to Security Information and Event Management. Instead of functioning as a siloed log management system, NetWitness SIEM is deeply integrated across the entire NetWitness Platform.
Here’s what sets it apart:
1. Built-In Enrichment from Network, Endpoint, and Logs
NetWitness SIEM doesn’t just collect logs, it correlates them with full packet capture and endpoint telemetry, offering richer, more actionable alerts.
2. Integrated Behavioral Analytics (UEBA)
Anomalous behavior isn’t just flagged; it’s understood in context. Whether it’s a user suddenly accessing sensitive files or an endpoint beaconing to a known bad domain, UEBA highlights what truly matters.
3. Cloud and Hybrid Visibility
NetWitness supports telemetry from modern cloud environments, containers, and SaaS applications, addressing a key blind spot in many legacy SIEM software.
4. High-Fidelity Alerting with Less Noise
Because it draws from multiple correlated sources, NetWitness SIEM software delivers fewer false positives and more signals that actually matter.
5. Tightly Integrated Response via SOAR
Security teams can pivot directly from detection to response using NetWitness Orchestrator, enabling faster triage and remediation without jumping between tools.
What this really means is NetWitness SIEM moves your organization from alert-driven firefighting to evidence-based decision-making and more effective incident response.

Key Takeaways for Security Leaders
So, what is SIEM, really?
It’s the hall of records for your SOC. But that’s only one piece of the puzzle. If you’re still relying on a traditional Security Information and Event Management as your primary defense, it’s time to rethink your architecture.
The modern SOC needs a platform that understands signals in context, reduces alert fatigue, and gives teams the agility to respond fast. NetWitness SIEM helps you do that by working as part of a larger threat detection and response ecosystem, not in a silo.
Final Thought
Your SIEM Security Information and Event Management should work with your broader security ecosystem, not despite it. As attackers evolve, your detection and response capabilities need to evolve too.
NetWitness SIEM is built for this reality, connecting the dots between logs, packets, and behavior to help you stop threats before they become incidents.
If your current SIEM Security Information and Event Management is making more noise than sense, it’s probably time for an upgrade.
FAQs: Enterprise Questions About SIEM
Q1: How is SIEM different from SOAR?
SIEM Security Information and Event Management collects and analyzes security data to detect threats, while SOAR (Security Orchestration, Automation, and Response) helps automate incident response workflows. They complement each other- SIEM detects, and SOAR acts.
Q2: Can I replace my SIEM with EDR or NDR?
Not entirely. EDR and NDR offer visibility into endpoints and networks, respectively, but they don’t handle centralized log management or compliance reporting like a SIEM does. They work best as extensions to SIEM, not replacements.
Q3: What’s the biggest reason SIEM deployments fail?
Many SIEM deployments struggle because they stop at installation. Without tuning, rule refinement, and use case development, even the most advanced SIEM will generate noise instead of insight. That’s why successful deployments, especially with NetWitness, often include professional services or expert-led onboarding. This upfront investment in design and configuration makes the difference between a tool that overwhelms and one that empowers.
Q4: How does behavioral analytics improve SIEM performance?
Behavioral analytics (UEBA) helps identify threats based on anomalies in user or system behavior, not just signature or rule matches. It makes SIEMs smarter and reduces false positives.
Q5: Is cloud SIEM better than on-premises SIEM?
It depends on your infrastructure. クラウドSIEM offer scalability and ease of management but may introduce data residency or integration challenges. A hybrid approach often works best.



