Every NDR vendor claims to offer complete network visibility, but dig deeper, and you’ll discover the devil lives in implementation details. Can their Network Traffic Analysis engine handle encrypted traffic at scale? Does their cloud network detection and response capability integrate with your specific cloud providers? Will their forensic threat detection work across your VPN tunnels, SD-WAN infrastructure, and container orchestration platforms? These aren’t abstract technical questions – they determine whether your chosen NDR solution becomes a security force multiplier or an expensive monitoring tool that generates more noise than insight.
Recent studies reveal enterprises lose an average of $4.9 million per data breach, with detection time being the primary cost driver. NDR solutions transform security posture by providing real-time visibility across cloud and on-prem environments. Through advanced traffic analysis and detection investigation response capabilities, organisations can identify threats in minutes rather than months, fundamentally shifting their security economics.
The real challenge: Network Visibility in hybrid and multi-cloud environments
Let’s break it down. Your business today isn’t confined to a single data centre. It runs workloads in AWS, Azure, and GCP, while still maintaining core systems on-prem. Teams use SaaS apps daily. Containers spin up and down in Kubernetes clusters. Traffic flows dynamically between VMs, cloud instances, and remote endpoints.
This fragmentation creates blind spots. Traditional security tools, built for fixed perimeters, miss east-west traffic within clouds or data centres. They struggle with ephemeral connections or encrypted flows. Attackers exploit these gaps to move laterally, escalate privileges, and exfiltrate data without triggering alarms.
That’s why visibility is everything. Your NDR needs to see traffic across:
- On-prem networks: Switches, routers, firewalls, and internal segments.
- Public clouds: VPC traffic mirroring, virtual taps, and native cloud integrations.
- Containers and microservices: Dynamic container networking layers.
- Remote and SaaS environments: VPNs, SD-WAN, and supported cloud APIs.
If your NDR misses even one of these, it leaves a door open.
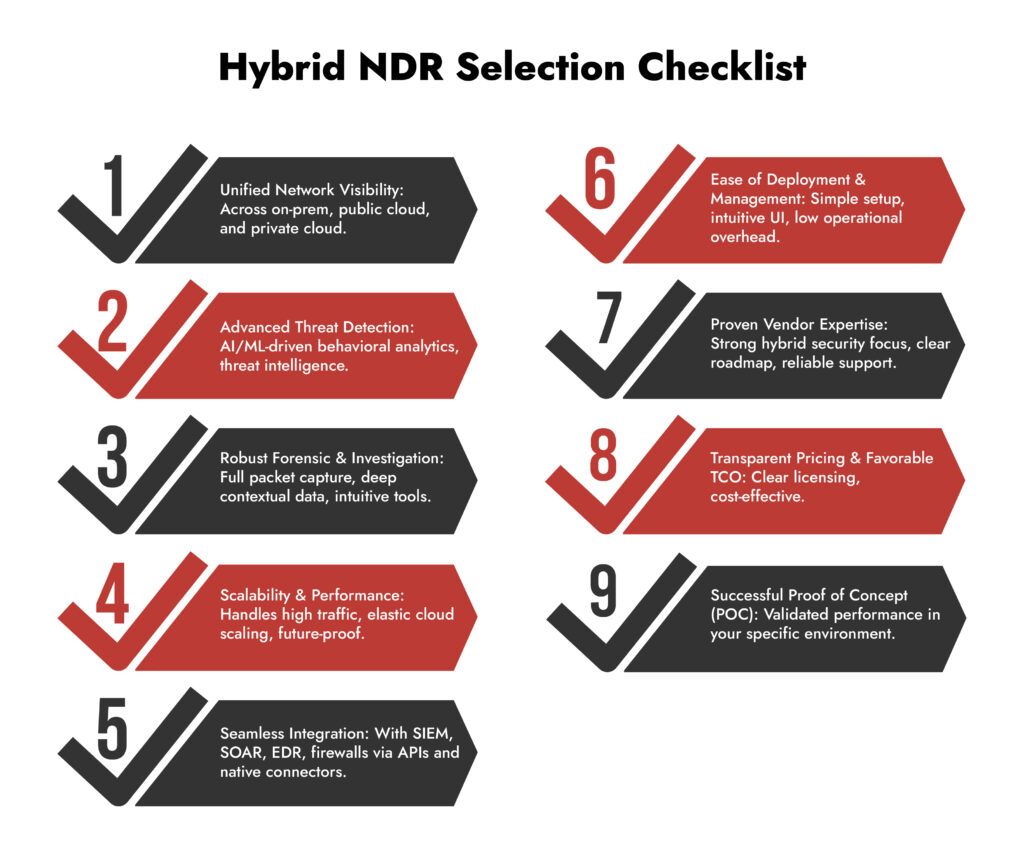
Five critical capabilities to look for in an NDR solution
1. Unified network traffic visibility across all environments
The core value of network detection and response is seeing everything. That means capturing and analysing traffic from on-prem data centres, hybrid environments, multi-cloud workloads, and containerised applications within a single platform.
Ask vendors: How do you aggregate data from these diverse environments into a central analysis engine?
2. Cloud-native deployment and scalability
Avoid solutions that simply lift-and-shift physical appliances to virtual machines. Your network detection and response should deploy cloud-native sensors that scale horizontally, minimise egress costs by analysing traffic locally, and support automated provisioning as your cloud footprint grows.
Ask vendors: What are your supported deployment models in AWS, Azure, and GCP? How do you handle scalability in auto-scaling environments?
3. Advanced behavioural analytics for east-west traffic
Signature-based detection alone won’t cut it. Effective NDR uses behavioural baselining to detect stealthy lateral movement, command-and-control traffic, and data exfiltration even when it uses encrypted or non-standard protocols.
Ask vendors: How do you detect threats in encrypted or ephemeral east-west traffic without generating high false positives?
4. Strong integrations with your existing security stack
Your network threat detection should seamlessly integrate with SIEMs, SOAR platforms, EDR/XDR tools, and ticketing systems. This ensures your SOC can pivot between network, endpoint, and identity telemetry for faster investigations and response.
Ask vendors: Do you offer out-of-the-box integrations with our current SIEM and SOAR? Can we orchestrate automated response actions based on network threat detection?
5. Encrypted network traffic analysis without full decryption
With over 80% of enterprise traffic encrypted, NDR solutions must analyse flows without introducing privacy risks or performance bottlenecks. Techniques like TLS fingerprinting, encrypted traffic metadata analysis, and behavioural correlation are key here.
Ask vendors: How do you analyse encrypted traffic at scale without decryption?
Common pitfalls to avoid
- Assuming cloud visibility is included: Many NDR vendors require separate licences or modules for each cloud provider.
- Overlooking deployment complexity: Ensure your team can deploy, configure, and maintain sensors without weeks of professional services.
- Ignoring cost models: Pricing based on bandwidth alone can explode in multi-cloud setups. Understand licensing tiers and scalability costs upfront.
Making your network threat detection selection count
Here’s the thing: selecting an network threat detection isn’t about ticking off features. It’s about choosing a solution that fits your architecture and security goals. Start by mapping your critical data flows across on-prem, hybrid, and cloud environments. Identify where visibility gaps exist today. Then evaluate vendors on their ability to fill these gaps with:
- Proven scalability
- Low operational overhead
- Actionable threat intelligence
- Fast, contextualised detections
Conclusion: Why NetWitness NDR solution stands out
Visibility gaps cost money, reputation, and customer trust. NetWitness NDR cybersecurity delivers pervasive network threat visibility by enabling organisations to monitor traffic centrally across on-prem, virtual, hybrid, and public cloud environments. Its flexible collection components, behavioural analytics, and advanced detection capabilities equip security teams to detect and respond to threats rapidly – no matter where they originate.
In a world where hybrid and multi-cloud are the norm, your NDR network should be the backbone of your detection strategy, not just another tool adding to the noise.
よくある質問
1. How does NDR security differ from traditional network security monitoring?
NDR security uses behavioral analysis instead of signature-based detection. Traditional tools look for known threats at network edges, while NDR security analyzes all communications to spot suspicious patterns, making it superior for detecting advanced threats and zero-day attacks.
2. Can network detection and response handle encrypted traffic?
Yes, NDR cybersecurity analyzes encrypted traffic through metadata and behavioral patterns without decryption. It examines connection timing, volume, and frequency to identify malicious activities hidden in encrypted channels.
3. How long does network detection and response software deployment take in hybrid environments?
Most organizations achieve initial monitoring within 2-4 weeks. Cloud components deploy faster (1-2 weeks) via API integration, while on-premises sensors may need additional setup time. Full optimization typically completes within 6-8 weeks.
4. How does NDR network pricing work for hybrid environments?
NDR network pricing combines traffic-based and infrastructure components. Cloud monitoring uses consumption-based pricing, while on-premises uses fixed licensing based on capacity. Many vendors offer hybrid models for predictable budgeting.



