UNC3886と可視性危機:ネットワーク検知・対応(NDR)が従来のセキュリティでは見逃していたものを明らかにする
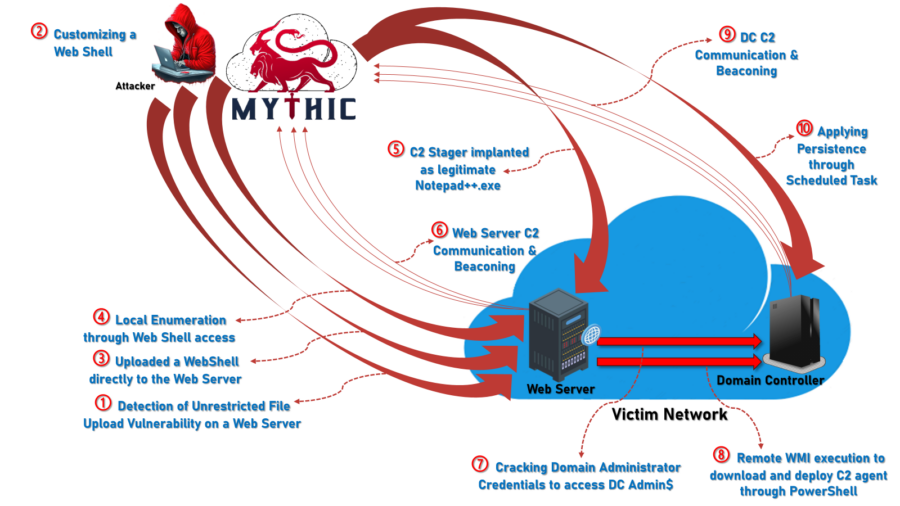
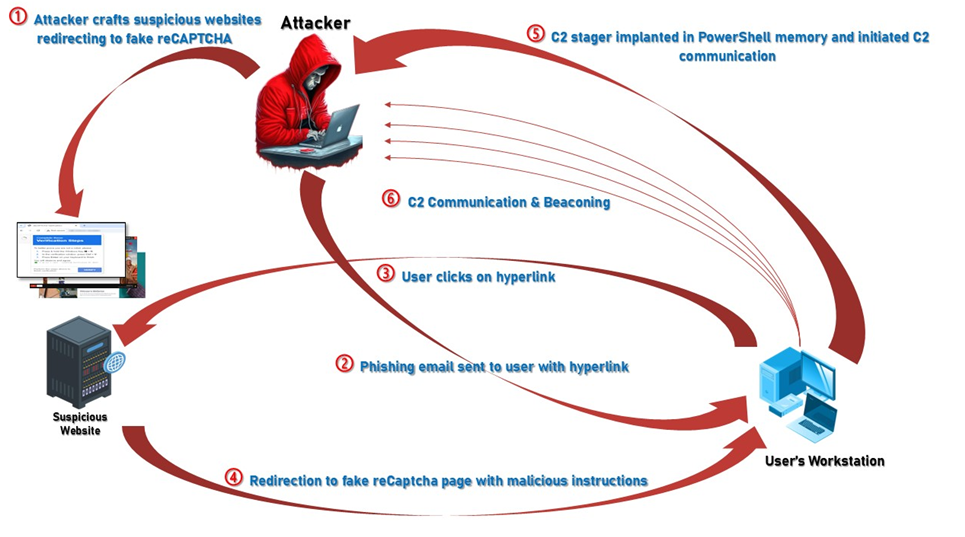
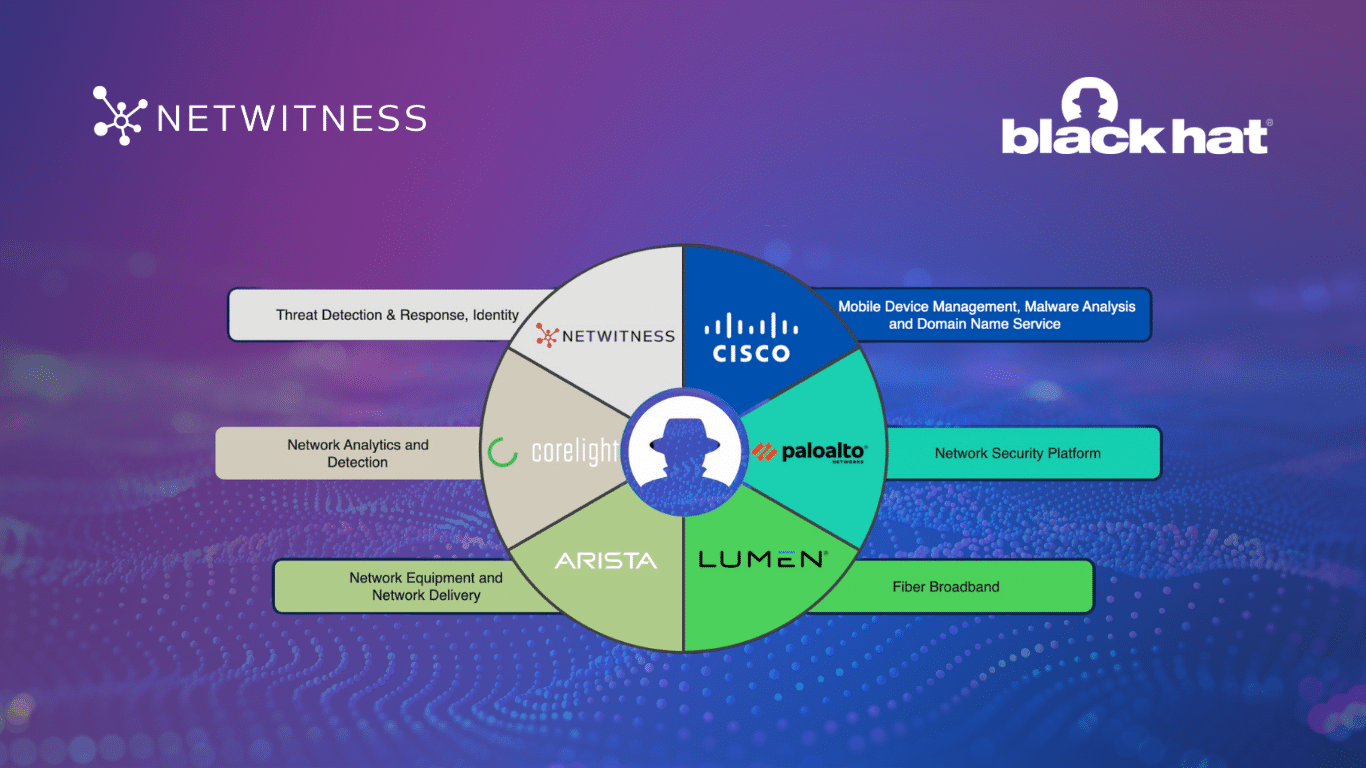
They don’t lock your files. They infiltrate your foundations. And if you’re relying on endpoint detection alone, you’re already playing catch-up. UNC3886 is a state-linked advanced persistent threat (APT) group that doesn’t behave like most attackers. Their goals aren’t financial. They’re strategic. And their playbook is built around one central idea: hide in the one place most defenses can’t see. This is the kind of threat that demands a shift in how cybersecurity leaders think about detection, response, and long-term resilience. Let’s break down what makes UNC3886 different and why Network Detection and Response NDR security is now critical for any enterprise protecting sensitive infrastructure. What Makes UNC3886 Different […]
もっと読む