What is an NDR Tool?
An NDR tool is a cybersecurity solution designed to monitor, analyze, and detect threats across all network activity – on-premises, in the cloud, or hybrid environments.
Unlike firewalls that focus on prevention or endpoint detection tools that monitor devices, network detection and response tools focus on what travels between those devices. They analyze every packet of network data to identify suspicious behavior, detect hidden attacks, and help teams respond quickly.
What this really means is that an NDR security tool provides the visibility most security teams don’t have – spotting signs of compromise before they become full-blown incidents.
Cyber attackers don’t always storm through the front door. More often, they move quietly through legitimate network traffic – blending in just enough to avoid detection. That’s why traditional firewalls and endpoint defenses alone aren’t enough.
To truly understand what’s happening inside your network, you need a system that sees everything. That’s where Network Detection and Response (NDR) tools come in.
Why NDR Security Tools Are Critical Today
Here’s the thing: enterprise networks are no longer simple. You’ve got cloud workloads, IoT devices, mobile endpoints, and remote users all connecting simultaneously. Each one expands the attack surface and each one introduces blind spots.
NDR security tools eliminate those blind spots. By continuously performing network threat monitoring, they analyze traffic patterns and flag irregularities that could indicate an intrusion.
A strong network detection and response tool offers:
- Real-time network visibility across every device and connection.
- Behavioral threat detection that identifies unknown or zero-day attacks.
- Automated response actions that cut down reaction time.
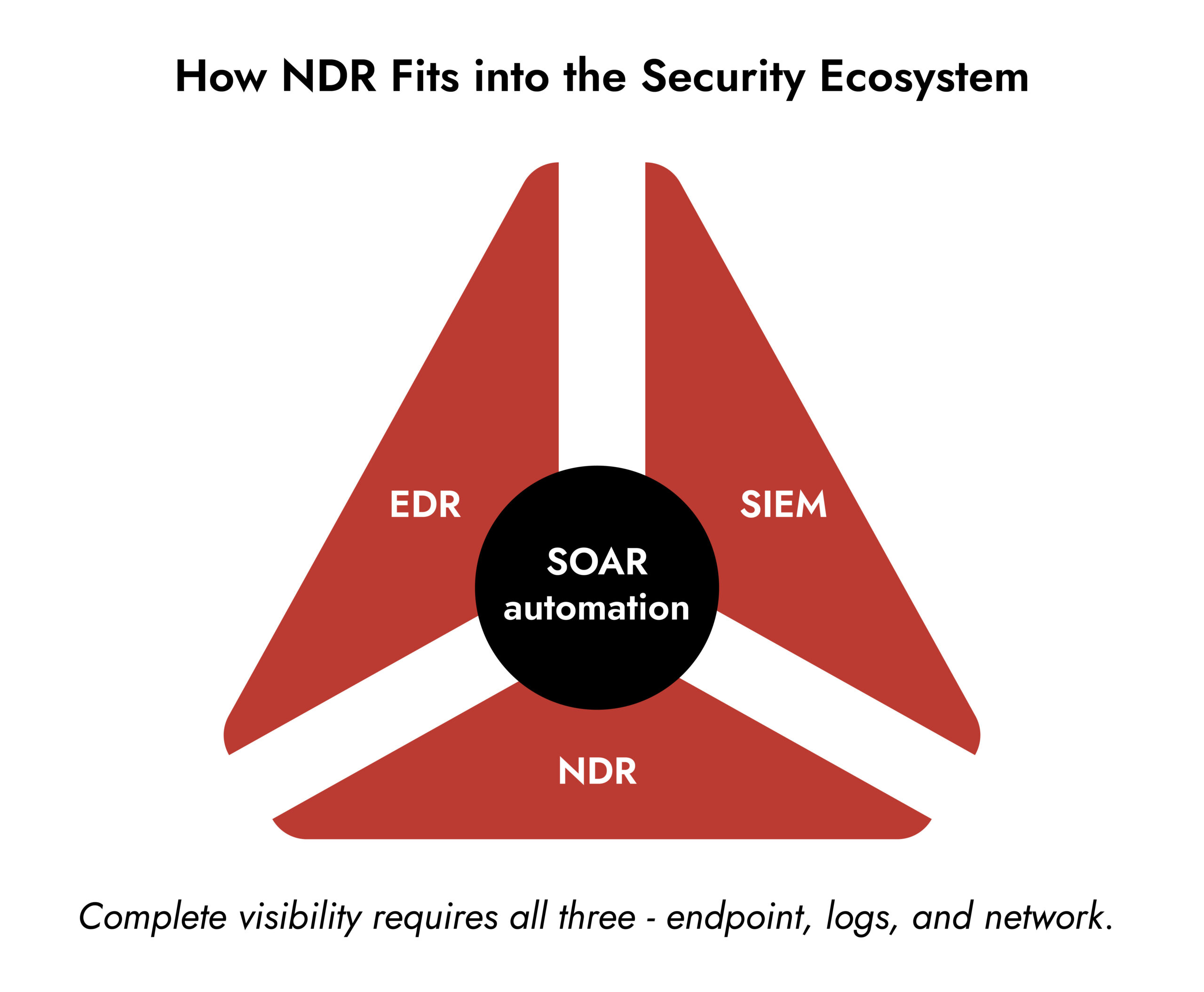
- Integration with SIEM, SOAR, and EDR tools for unified threat detection.
In short, NDR tools help security teams find the threats that others miss.
How Network Detection and Response Tools Work
Every network detection and response tool follows the same core approach: visibility, analysis, detection, and response.
- Data Collection – The NDR system captures network traffic (full packets or flow data) from sensors or taps across the environment.
- Baseline Learning – It uses analytics and machine learning to understand what “normal” looks like.
- Threat Detection – When deviations occur – like unusual data movement or suspicious command-and-control activity – alerts are triggered.
- Investigation and Response – Analysts can replay sessions, trace attack paths, and collaborate with other tools to contain threats fast.
Because it doesn’t rely on predefined signatures, an NDR tool can catch even those stealthy, never-seen-before threats that slip past other defenses. 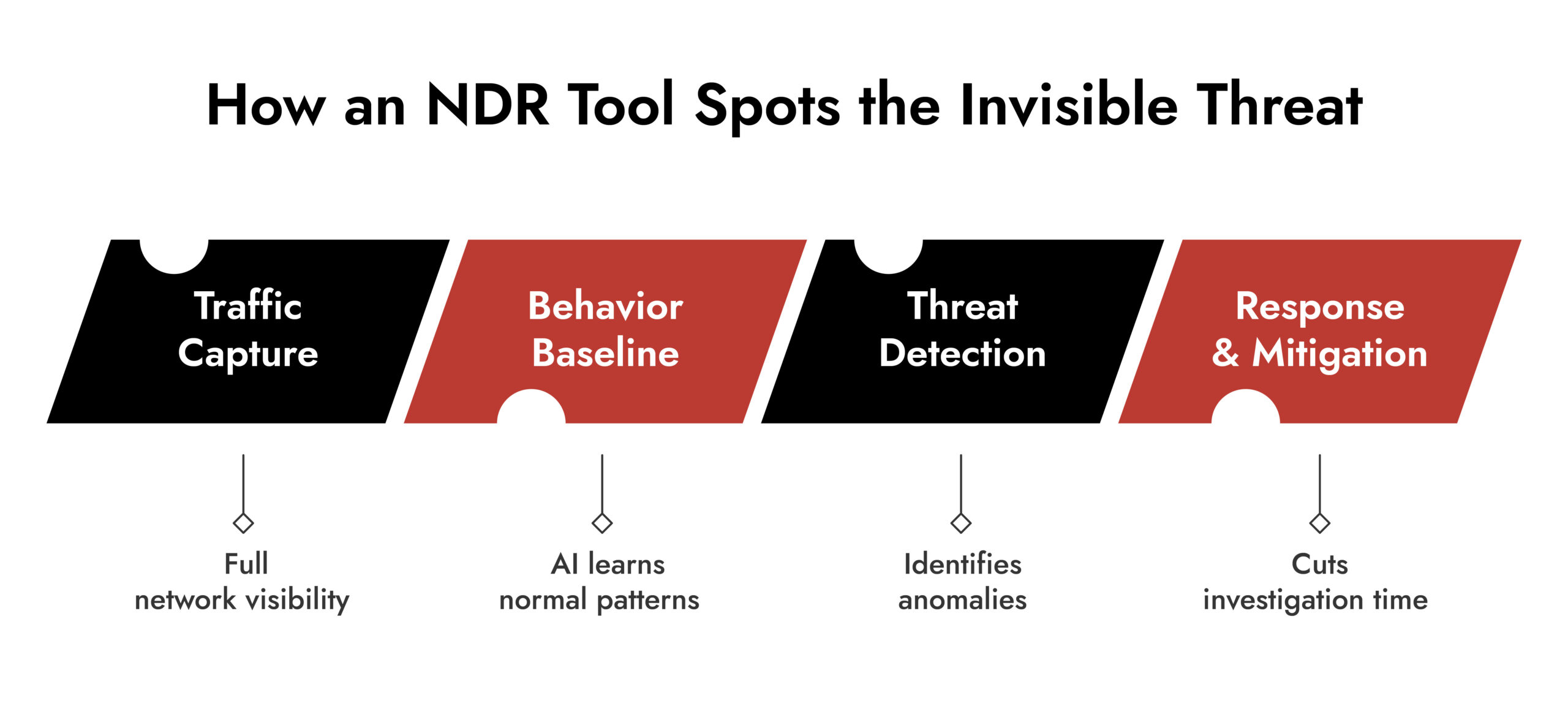
6 Types of Threats Detected by NDR Tools
Not all threats are created equal and not all are visible to traditional security tools. Here are six key attack types that the best network detection and response tools can uncover:
1. Lateral Movement: Once inside, attackers move from one system to another. NDR tools identify unusual internal traffic signals and lateral spread.
2. Command-and-Control (C2) Communication: Attackers often communicate with external servers. Network detection response tools can spot these covert channels by detecting irregular outbound patterns.
3. Data Exfiltration: When sensitive data starts leaving your network in unexpected volumes or directions, NDR tools raise the alarm.
4. Insider Threats: NDR systems track user and host behavior, revealing insider misuse or credential theft.
5. Encrypted Traffic Abuse: Even encrypted traffic can be analyzed for anomalies, allowing NDR security tools to detect malicious behavior hidden in SSL/TLS channels.
6. Ransomware Propagation: By analyzing connections in real time, an NDR tool can spot ransomware lateral spread early, before encryption causes widespread damage. 
Key Features of the Best Network Detection and Response Tools
The best network detection and response tools combine automation, analytics, and scalability. Here’s what to look for when evaluating one:
| Feature | Why It Matters |
| Full-Packet Capture | Enables deep forensic analysis of every connection. |
| Machine Learning Detection | Identifies subtle anomalies without relying on signatures. |
| Integration with SOC Stack | Works seamlessly with SIEM, EDR, and SOAR systems. |
| Threat Intelligence Feeds | Keeps detection rules updated with the latest indicators. |
| Cloud and Hybrid Coverage | Monitors activity across all environments. |
| Automated Response Actions | Shorten time from alert to containment. |
A high-quality NDR security tool doesn’t just detect – it interprets and responds in real time, helping SOC teams prioritize real threats over noise.
Building a Stronger Security Posture with NDR
Here’s what it comes down to: the more you can see, the faster you can act. Network detection and response tools give security teams the ability to:
- Detect stealthy intrusions.
- Investigate efficiently with network evidence.
- Reduce response time through automation.
- Strengthen collaboration between security operations and IT teams.
Combined with other platforms like EDR and SIEM, NDR tools create a layered defense strategy that gives organizations full visibility from endpoint to network edge.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.

Choosing the Right NDR Tool for Your Organization
Selecting the right network detection and response tool depends on your organization’s size, architecture, and goals. Consider:
- Scalability – Can it handle growing data volumes and hybrid networks?
- Ease of Integration – Does it work with your existing SIEM or SOAR?
- Detection Accuracy – How well does it reduce false positives?
- Forensic Depth – Can it replay sessions or trace attack paths clearly?
- Automation Capabilities – Does it streamline investigations or trigger responses automatically?
The best network detection and response tools will not just fit your environment, they’ll enhance it.
Where NetWitness Fits In
If you’re exploring NDR security tools, NetWitness NDR stands out for its deep packet inspection, behavioral analytics, and integration of flexibility. It doesn’t just alert, it correlates events, surfaces context, and accelerates response.
With NetWitness Network Detection and Response, you get:
- End-to-end network visibility across on-prem, cloud, and hybrid setups.
- AI-driven anomaly detection to uncover hidden threats.
- Seamless integration with NetWitness SIEM, SOAR, and EDR.
- Scalable performance designed for modern SOCs.
What this really means is that NetWitness helps your team detect earlier, investigate smarter, and respond faster, all while reducing noise and blind spots.
Conclusion
Attackers keep evolving, but so can your defenses. Network detection and response tools give organizations the power to uncover what’s hidden, investigate precision, and respond with confidence.
And when combined with advanced platforms like NetWitness NDR, your SOC gains not just visibility but actionable intelligence – turning every packet into insight and every anomaly into an opportunity to defend smarter.
Frequently Asked Questions
1. What is an NDR tool?
An NDR tool (Network Detection and Response tool) monitors network traffic for signs of malicious activity, helping detect and respond to cyber threats faster.
2. How can NDR be integrated with other cybersecurity tools?
Most NDR security tools integrate with SIEM, SOAR, and EDR platforms. This allows organizations to unify detection data, automate workflows, and improve overall threat response.
3. Which network detection and response tool are best for security?
The best network detection and response tools are those that combine full network visibility, behavioral analytics, and strong integration, like NetWitness NDR, which provides all three in a single platform.
4. Which NDR tool is right for you?
That depends on your environment. Look for an NDR tool that scales easily, offers strong analytics, and aligns with your broader security architecture.




