Introduction
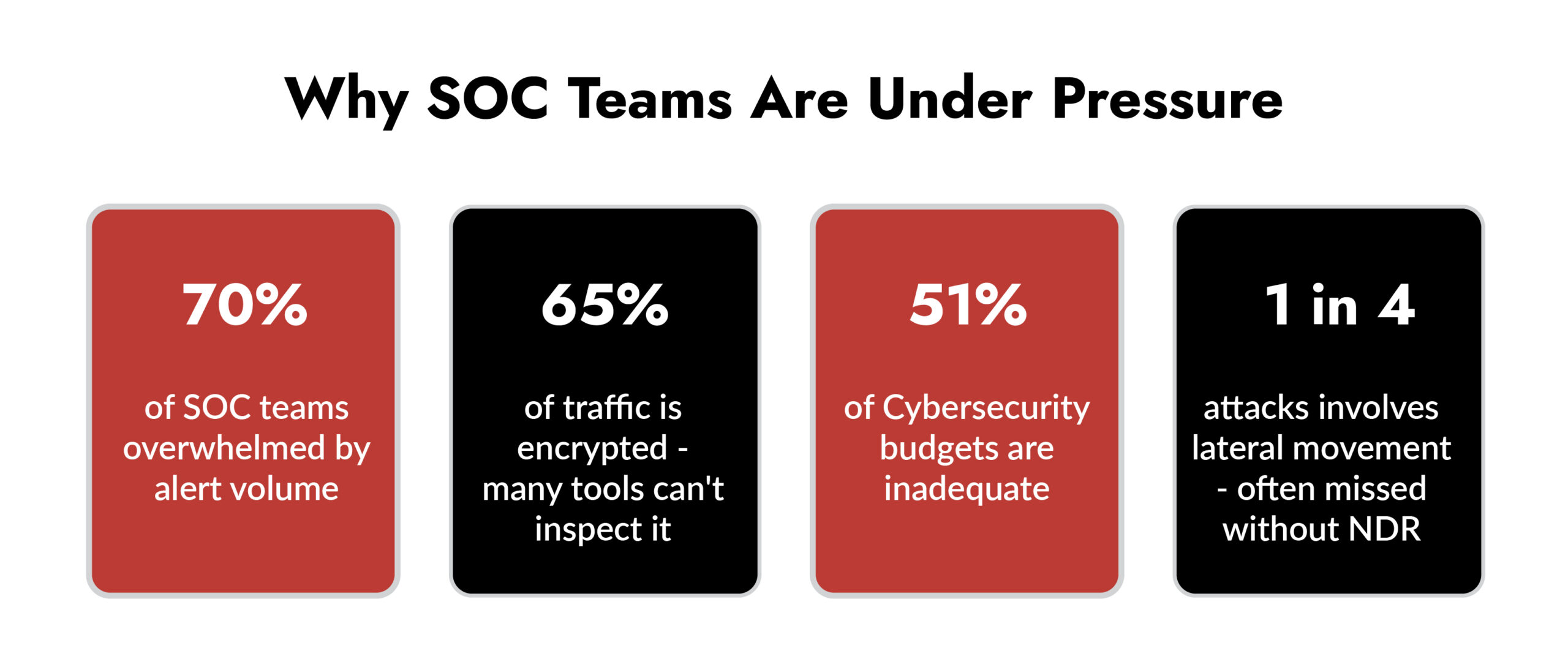
Security Operations Centers (SOCs) today are overwhelmed, not just by increasingly sophisticated threats, but also by operational fatigue, resource limitations, and an ever-expanding attack surface. A recent report revealed that 70% of SOC teams feel emotionally exhausted by the volume of alerts, while 51% of cybersecurity budgets fall short of covering essential requirements.
At the heart of this struggle lies a critical gap between threat detection and timely action. This is where Network Detection and Response (NDR) steps in. Specifically, NDR in cybersecurity enables real-time visibility, rapid cyber threat detection, and actionable network intelligence, empowering SOC teams to respond faster and smarter.
Why SOCs are Struggling to Keep Up
Let’s start with a reality check. Most security teams today grapple with five persistent challenges:
Extended Attacker Dwell Time:
Cyber attackers often remain undetected in enterprise environments for days or even months, using stealth techniques like lateral movement and data staging. Without advanced network threat analytics, these movements often go unnoticed.
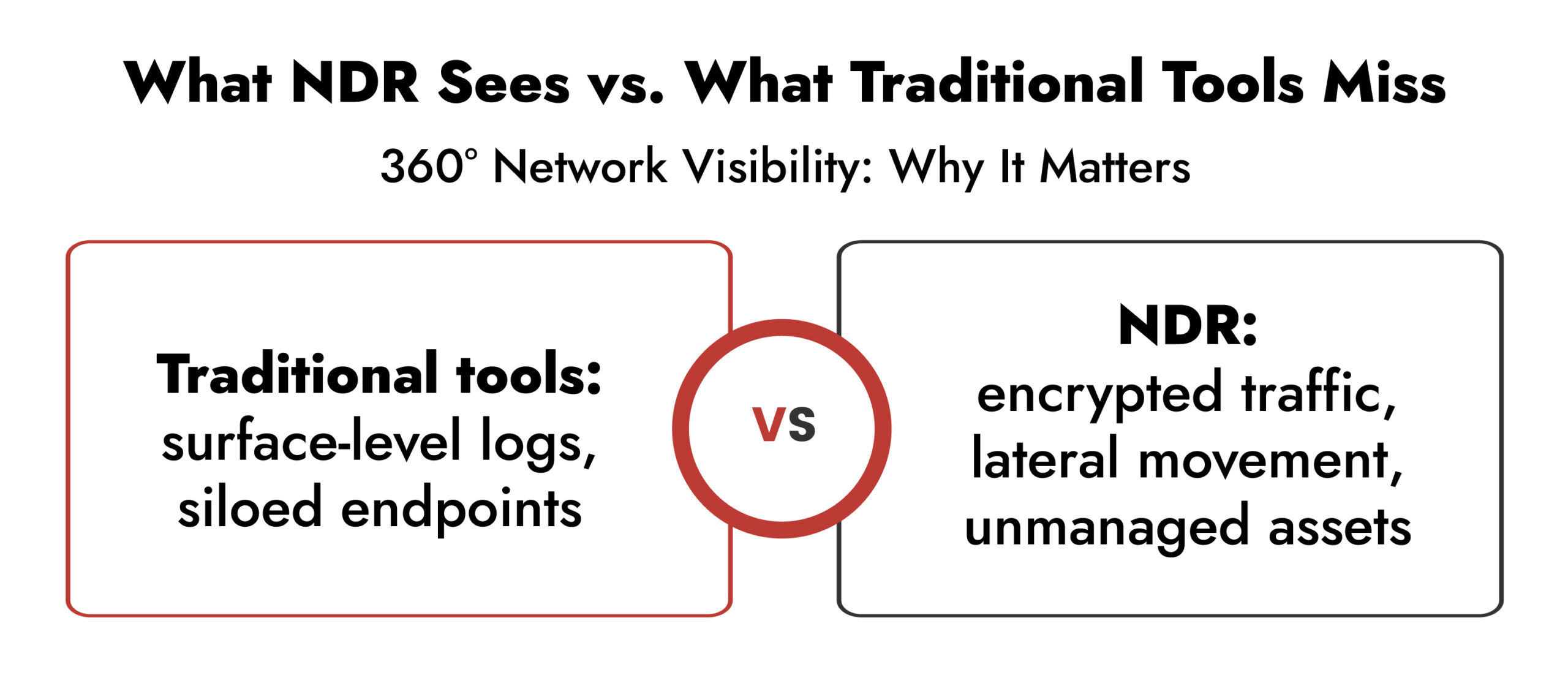
- Lack of Network Visibility:
Traditional tools operate in silos, providing fragmented insights. Without comprehensive network visibility, SOCs can’t correlate events across cloud, on-premises, and hybrid environments, making blind spots a constant risk.
Alert Fatigue:
SOCs are flooded with alerts, many of them redundant or irrelevant. This results in analyst burnout and missed signals. Without a system that streamlines threat detection investigation response, it’s difficult to prioritize real threats.
Encrypted Traffic Blind Spots:
With over 90% of internet traffic now encrypted, adversaries increasingly hide malware and command-and-control (C2) communications within SSL/TLS sessions. Traditional tools often fail to detect these threats.
NDR solutions that support encrypted traffic analysis without full decryption restore visibility into these blind spots, helping SOC teams spot anomalies, detect advanced threats, and take action before damage is done.
Shadow IT and Unmanaged Devices:
BYOD and hybrid work environments have led to a proliferation of unauthorized devices. These endpoints introduce new vulnerabilities, making real-time cyber threat detection across the entire network a must.
What Is NDR in Cybersecurity?
NDR in cybersecurity refers to solutions that monitor, analyze, and respond to suspicious network activity in real time. Instead of relying only on signature-based alerts, NDR solutions detect subtle anomalies using behavior-based models, threat intelligence, and contextual analytics.
NetWitness is an industry leader that provides network visibility across cloud, virtual, and physical environments. It collects data from full-packet capture, NetFlow, metadata, and logs, allowing security teams to address threats at every stage of the threat detection investigation response cycle.
Real-Time Analytics: The Key to Modern SOC Efficiency
Here’s how a robust NDR in cybersecurity setup supercharges SOC productivity:
1. Continuous Cyber Threat Detection:
By continuously analyzing traffic for signs of malicious behavior, NDR detects lateral movement, beaconing, exfiltration attempts, and C2 communications. These capabilities are essential for cyber threat detection that goes beyond surface-level signatures.
NetWitness enhances this by applying real-time analytics to identify deviations from baseline behavior, providing SOCs with smarter, faster alerts.
2. Streamlined Forensic Investigation:
The network forensic depth offered by NDR tools is unmatched. Instead of looking at scattered logs, analysts can reconstruct entire attack sessions. This allows for faster root-cause analysis and incident response.
NetWitness NDR solution provides:
- Full-packet capture.
- Metadata enrichment.
- Session replay functionality.
- Support for encrypted traffic analysis.
These features reduce MTTU (Mean Time to Understand) and allow deep retrospective analysis using powerful network threat analytics.
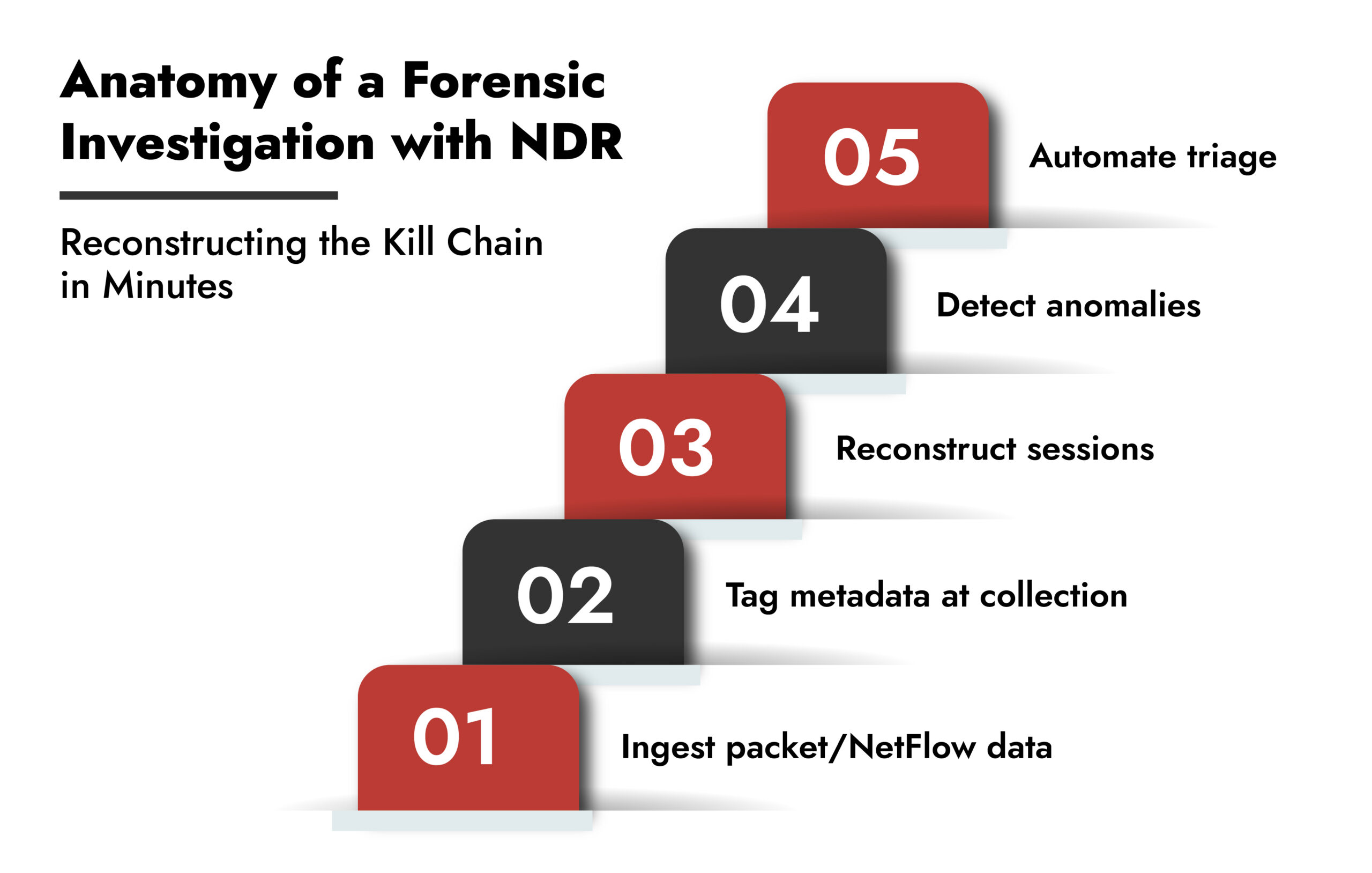
3. Reconstructing the Kill Chain in Minutes:
- Ingest packet/NetFlow data.
- Tag metadata at collection.
- Reconstruct sessions.
- Detect anomalies.
- Automate triage.
4. Faster, Contextual Response:
NDR in cybersecurity plays a vital role in reducing MTTR. By unifying alerts and contextualizing data, SOCs can triage events more effectively and automate workflows.
With NetWitness, teams can:
- Use prebuilt playbooks for response automation.
- Correlate alerts across SIEM, EDR, and log sources.
- Prioritize based on asset value and threat severity.
The result? A leaner, faster threat detection investigation response loop.
5. Network Visibility Without Gaps:
Network visibility is the backbone of effective threat detection.
NDR network allows analysts to see both north–south and east–west traffic, including encrypted or virtualized traffic.
NetWitness NDR solution delivers:
- Visibility into all connected assets, including IoT and shadow IT
- In-depth traffic monitoring across multi-cloud and hybrid environments
- Threat context layering for every network session
By bringing encrypted sessions, unmanaged devices, and lateral threats into view, NDR in cybersecurity reduces blind spots significantly.
How NDR Supports Proactive Threat Hunting
The best SOCs don’t just wait for alerts; they hunt threats proactively. Network threat analytics plays a pivotal role here.
Advanced NDR platforms like NetWitness support threat hunters by offering:
- Historical data archives for deep proactive threat hunting.
- Behavioral analytics that detect subtle changes in user and entity behavior.
- Advanced query engines to track down suspicious sessions.
This proactive model transforms SOC from a reactive unit into an intelligence-driven command center.
Why NetWitness NDR Stands Apart in the Market?
According to the latest Gartner Market Guide, NetWitness is recognized for its:
- World-class forensic capabilities.
- Scalable architecture.
- Flexibility in complex environments.
- Strength in automation and managed services.
NetWitness NDR network delivers real-time network threat analytics, contextual visibility, and seamless integration with other SOC tools like SIEM and EDR.
Whether you need to stop ransomware, hunt for APTs, or improve day-to-day operations, NetWitness ensures your SOC can perform at scale, making it one of the best NDR tools in the market.
Real-World Impact of Network Detection and Response
Let’s compare the SOC before and after implementing an advanced NDR in cybersecurity strategy:
| Metric | Without NDR | With NDR |
| MTTD (Detection Time) | 20+ days | < 6 hours |
| MTTR (Response Time) | Days | Minutes to Hours |
| False Positive Rate | High | Significantly Lower |
| Analyst Fatigue | Common | Reduced |
| Network Visibility | Fragmented | Unified, Encrypted & Real-Time |
Conclusion: Scaling Your SOC with Confidence
Security teams today must balance visibility, speed, and precision. NDR in cybersecurity is a force multiplier that helps SOCs stay one step ahead.
From cyber threat detection to proactive hunting and enterprise network threat analytics, NetWitness NDR delivers the depth and context security teams need to operate with confidence.
Whether you’re defending against zero-day threats or eliminating operational fatigue, NDR in cybersecurity, powered by NetWitness, gives you the visibility and control to act before damage is done.
Ready to empower your SOC with better visibility and faster response? Explore NetWitness NDR network.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.

Frequently Asked Questions
1. What is NDR in cybersecurity?
NDR in cybersecurity refers to continuous monitoring, detection, and response across network traffic. It’s particularly useful for identifying lateral movement, encrypted attacks, and insider threats.
2. How is NDR different from SIEM or EDR?
SIEM aggregates logs and alerts. EDR focuses on endpoints. NDR fills the gap by watching the network, offering behavioral insights into communications between devices.
3. Can an NDR solution handle encrypted traffic?
Yes. NetWitness NDR uses metadata and behavioral analytics to analyze encrypted traffic without needing to decrypt it.
4. What is network threat analytics?
Network threat analytics refers to using AI, behavior models, and context to analyze network traffic and identify threats based on how data moves.
5. Does NDR specialists require a rip-and-replace approach?
Not with NetWitness. The platform integrates with your existing infrastructure.
6. Does NDR replace other security tools?
No. Solutions like NetWitness NDR integrate with SIEM, EDR, and SOAR systems.




