In cybersecurity, chaos isn’t rare; it’s business as usual. Threats evolve faster than most defenses can adapt. And if your detection and response approach is scattered across disconnected tools, silos, or teams, you’re not just behind; you’re exposed.
A unified threat detection and response strategy isn’t nice to have. It’s survival. Here’s how to build one that actually works.
What is threat detection and response?
Threat detection and response (TDR) is the continuous process of identifying malicious activity in your environment and taking action to stop it. That includes detecting everything from known malware to unknown threats that don’t match any signatures and responding in a way that contains damage, closes gaps, and learns from every incident.
How does threat detection and response work?
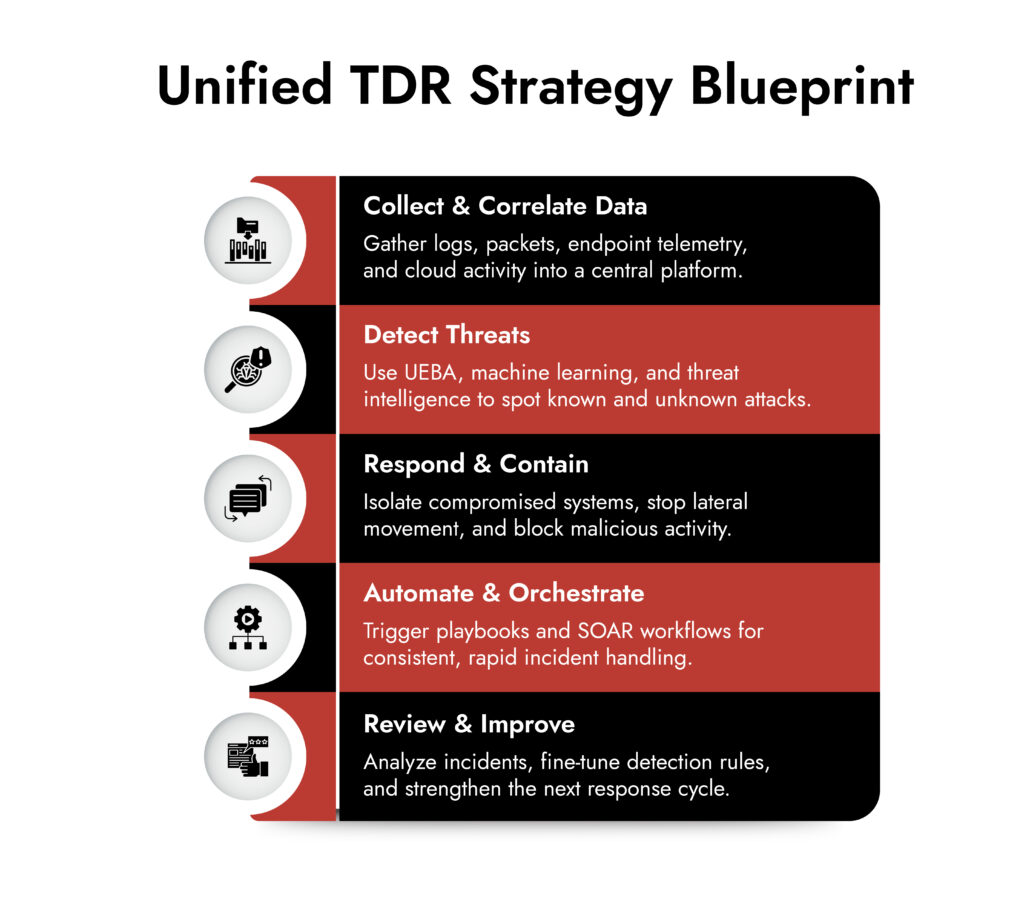
It starts with visibility. If you can’t see what’s happening across your network, endpoints, users, and cloud assets, you’re flying blind. Then comes context enriching that data with threat intelligence and behavioral analytics. Finally, response: automated where possible, guided by analysts where necessary.
This sounds simple on paper. In practice, it’s anything but.
Why “Unified” Matters
Fragmented tools and alert fatigue are killing security teams. According to the Ponemon Institute, 61% of security teams say they struggle to prioritize alerts due to high volumes. And nearly half of all cybersecurity professionals admit they’ve ignored alerts that later turned out to be legitimate threats.
That’s not incompetence. That’s overload.
A unified threat detection and response strategy consolidates visibility, context, and action into one coordinated system. Instead of jumping between tools or drowning in noise, analysts work from a single source of truth, with one set of workflows.
The Stakes? Higher Than Ever
How serious are cyber threats today? Consider this: nearly 1 billion email addresses were exposed in a single year. That statistic isn’t just theoretical it affected 1 in every 5 internet users. And the financial hit for businesses is just as brutal. In 2024, the average cost of a data breach hit $4.88 million.
Every hour lost in detection or response doesn’t just cost money, it costs trust, uptime, and in many cases, compliance. Solutions like NetWitness 탐지 AI help teams surface high-risk anomalies in real time, reduce false positives, and respond faster, turning every alert into actionable insight.
Best Practices for Building a Unified Threat Detection and Response Strategy
Here’s what it takes to get it right:
1. Start with Full Spectrum Visibility
You can’t defend what you can’t see.
A unified TDR platform should ingest data across network traffic, endpoints, cloud workloads, user behavior, and external threat intel. Not in separate panes. In one view.
Why? Because modern threats don’t stay in one lane. A phishing email might lead to credential theft, which then enables lateral movement inside your network. If your tools only catch one piece of that chain, you miss the full picture.
Cyber threat detection and response depends on seeing across all vectors in real time.
2. Use the Right Detection Techniques Not Just Alerts
Traditional signature-based detection isn’t enough. You need multiple techniques working together, including:
- 사용자 및 엔티티 행동 분석(UEBA) to catch unusual activity
- Machine learning models to flag anomalies
- Threat intelligence integration for real-time context
- Packet and log inspection to validate suspicious behavior
These 위협 탐지 and incident response techniques should operate side by side, enriching each other. False positives go down. Detection speed goes up.
3. Automate the Mundane. Keep Humans for the Complex.
Your analysts should be threat hunters, not button pushers.
Invest in threat detection and response tools that support automation playbooks, correlation rules, and automated enrichment. This frees your human experts to focus on real investigation and decision-making.
When alerts are triaged automatically and only the critical ones bubble up, your team isn’t chasing ghosts, they’re closing gaps.
4. Response Should Be Built-in, Not Bolted On
A common mistake? Treating a response like a separate function that kicks in after detection.
In a unified strategy, detection and response are linked. The moment a threat is detected, response workflows begin whether that’s isolating a machine, disabling an account, or triggering forensic capture.
This is where cybersecurity incident response services (or internal playbooks) come in. The goal: minimize dwell time. The longer a threat lives in your environment, the more damage it does.
5. Measure What Matters
Alert volume means nothing. Dwell time, containment speed, mean time to detect (MTTD), and mean time to respond (MTTR) these are the metrics that matter.
A mature threat detection and response strategy tracks and improves these continuously.
Too many organizations focus on how many threats they catch. The better question is: how long were they there before you found them, and what did they do in the meantime?
When to Consider Threat Detection and Response Services for Businesses
Not every organization can sustain a fully staffed, 24/7 security operations center. That doesn’t mean protection has to slip. This is where threat detection and response services for businesses add real value.
By leveraging the right threat detection and response tools, organizations gain:
- Continuous monitoring across endpoints, cloud environments, and networks
- Real-time detection enriched with analytics and intelligence
- Expert-led investigation and containment aligned with cybersecurity incident response services
- Enterprise-grade cyber threat detection and response without the overhead of building everything in-house
The question isn’t just what is threat detection and response, but also how does threat detection and response work at scale when resources are tight. The answer is a unified approach—whether managed internally, supported externally, or delivered as a hybrid.
Done right, it ensures threats are detected faster, responses are immediate, and business impact is minimized.
NetWitness: Built for Unified Threat Detection and Response
If you’re looking to move beyond fragmented security operations, NetWitness is purpose built for this shift.
Here’s what sets it apart:
- Unsurpassed Visibility: NetWitness collects data across endpoints, users, networks, and cloud giving you a complete picture.
- Faster Threat Detection: Realtime enrichment at the point of capture with threat intelligence and business context speeds up detection and response.
- Smarter Analytics: Integrated UEBA, machine learning, and automation means your team hunts threats, not alerts.
- One Interface: All data, context, and response tools in one platform. No toggling. No guesswork.
NetWitness is more than a tool. It’s a unified platform for modern cyber threat detection and response.
If your current setup is giving you more noise than clarity, it’s time to rethink your strategy and your tech.
자주 묻는 질문
1. What is threat detection and response?
It’s the ongoing process of identifying malicious behavior and taking timely action to stop or contain it. The goal is to minimize impact, reduce dwell time, and improve threat resilience.
2. How does threat detection and response work?
It combines visibility (collecting data), detection (using analytics and intel), and response (automated and manual actions) into one integrated workflow. The more unified this process is, the faster and more effective your outcomes are.
3. What are some common threat detection and incident response techniques?
Techniques include signature-based detection, behavior analytics (UEBA), anomaly detection via ML, threat intelligence correlation, and packet/log analysis. These techniques are often layered for maximum coverage.
4. What tools are used in cyber threat detection and response?
SIEMs, EDRs, NDRs, and SOAR platforms are commonly used. Platforms like NetWitness integrate many of these capabilities into a single ecosystem.



